Continuation at a tangent to [stderr]
Tools like Palantir are the tip of an iceberg: a gigantic iceberg of data. In case you don’t know, when organizations like the NSA are talking “big data” they are talking “yottabytes.” i.e.:
The Pentagon is attempting to expand its worldwide communications network, known as the Global Information Grid, to handle yottabytes (1024 bytes) of data. (A yottabyte is a septillion bytes—so large that no one has yet coined a term for the next higher magnitude.) [wired]
It’s probably not ‘yottabyte’ scale, it’s just ‘exabyte’ scale, but the people who poo-poo the storage capacity of these systems do not understand how megastorage works. Yottabytes are achievable because the basic algorithms scale and the searches parallelize. “It’s just a matter of money” in other words.
An exabyte is a million terabytes. Twitter uses twenty terabytes to back up every tweet that has ever been sent (what, do you think they delete them?) Some estimates of the data-size of the US Library of Congress put it in the range of fifteen to twenty terabytes depending on the scan-resolution and compression of images. So, if NSA’s storage vault is holding a couple exabytes, it’s holding several million times what the Library of Congress has ever held, and probably Twitter and Facebook and a whole lot more. One thing it for damn sure isn’t holding is “just” metadata. Metadata compresses supremely well – I’d predict about 75% or more depending on how it’s indexed and clustered. You could hold all the metadata for all the calls in the US on a hundred terabytes or so. Twitter is 200 billion tweets/year, but SMS texting is 600 billion per day. (All numbers should be considered rough but within an order of magnitude) Of course what the collectors are doing is pruning obviously machine-generated content: banner ads, spam, etc – no need to keep that, and that’s 90% of email. Anyway, you don’t build a megastorage system if all you’re collecting is metadata; you do that when you’re building a rolling window through a vast dataset.
![Hierarchical Storage Management [source]](https://freethoughtblogs.com/stderr/files/2017/03/HSM_Cover_w_500.jpg)
Hierarchical Storage Management [source]
If you were building an AI, you’ve already got a couple of elements of cognition built into the underlying architecture: relevance (based on refresh interval) the ability to do cognition-within-a-tier (like human short term versys long term memory) and the ability to recognize that you know something about something, to do faster retrieval. In computer databases, that’s done with bloom filters or a primary index: you may not know (yet) what you know about Marcus Ranum’s text messages, but you know you know something about Marcus Ranum because a probe for that name returned that you have 3,281,238 items in various stages of your cache. If you’ve got some time, experiment a bit by thinking about how you retrieve information: have a friend who knows you somewhat sit down with you, write a few “flash cards” with some things for you to remember, and then experience the remembering. Be aware of the layers in which memories cascade into your mind and observe which ones come all at once, which are most recent, which are flagged with a jot of adrenaline, etc. By the way, another fun game you can play when you’re doing this is for your tester to make two “comparable” lists and have you drink 2 shots of alcohol between the runs. Experience the difference – it may be remarkable. (By “comparable” lists I mean stuff like: “what was your first pet” and “what color was your first bicycle” that go back to about the same time period and similar emotional loading)

each of those cartridges is a whole lot of bytes
But here’s the crazy thing: a megastorage system scales cleanly with Moore’s law, more or less, and doesn’t require a lot of intervention to upgrade. I did some work, in 2009, at San Diego Supercomputer Center, looking at data on their High Performance Storage System (HPSS) and – at that time – the tape robot managed 5 petabytes of data. A year later, they upgraded the tape drives to drives that could back-read the old tape cartridges but could store 4 times as much data on a cartridge. Instantly, the total capacity of the storage system was 20 petabytes! Presto!
When you upgrade the tape drive the total capacity goes up, and the robot starts a process of grabbing the 4 oldest tapes, copying them to the hard drive cache array, then ejects the old tapes (which go into a vault somewhere) and compresses all the data from the 4 tapes to a new tape. That’s done without updating the “memory” score of the data, of course, or the storage array would be experiencing false memory flashes like we ageing humans do.
Who do you think IBM builds things like the TS3500 Tape Library[ibm] for? (Our motto: “IBM Global Financing can help!”) The computing industry has served the military/industrial police state since the manhattan project – they evolved together, in fact. This is no mere dalliance, it’s a marriage of true love forever.
Back in the day, when I was a young systems pup working on the Human Genome Mapping project (at Welch Medical Library, via Howard Hughes Medical Institution and the National Library of Medicine) we were worrying about how to store and search through human genomes. Well, at about a terabyte per human, if the NSA’s megastore can hold 7 exabytes – i.e.: it has 4 of those IBM TS3500s – it could back up all of our genomes. All of humanity’s. That’d be some metadata indeed.
But we know it’s being used for the basic stuff: every message, posting, comment, tweet, txt, call record, and financial transaction. And, of course, it’s full of images. Jennifer Lawrence, Scarlet Johansson, Benedict Cumberbatch, and I, as well as pretty much everyone who has ever pointed their phone’s camera at their face: that’s all in there too, in various states of deshabille. How good do you think the protections are on that data, by the way? And what do you think of facial recognition software? Most people know it’s not super reliable and it’s sometimes mostly right, and you can go on facebook and mark a picture as “this contains an image of Marcus Ranum” or whatever. How convenient. And (as I’ve mentioned elsewhere) [stderr] data is collected to be combined: suppose you take a license plate reader’s scan of my car leaving the extended parking at Dulles airport, then you can be pretty sure there’s a good chance one of the operators is the owner: then you can fuse that information with the drivers license photo database (why do you think they switched to digital for all of that?) and a passport database (ditto) and now you have a rock-solid multi-point baseline from which you can probably accurately identify Marcus Ranums in pictures on the internet. You’ve also got border entry/exit point face recognition.
It’s hard to estimate how many facial recognition images are currently in various government databases, but I would predict they are severely underestimated because of things like facebook profile pictures and tagged selfies. Some estimates are in the range of 400 million in the FBI database alone. So, when the FBI serves a warrant for #NODAPL protesters, and gets the names, they can scrub the names against the license picture databases and then scrub those images against any footage they’ve got of a protest (excuse me, “terrorism”) [atlantic]
Police departments in nearly half of U.S. states can use facial-recognition software to compare surveillance images with databases of ID photos or mugshots. Some departments only use facial-recognition to confirm the identity of a suspect who’s been detained; others continuously analyze footage from surveillance cameras to determine exactly who is walking by at any particular moment. Altogether, more than 117 million American adults are subject to face-scanning systems.
That puts a new spin on “watch list” doesn’t it? But, remember: “walked through Dulles Airport security at ${date}” is just metadata.
Courts haven’t determined whether facial recognition constitutes a “search,”
Color me shocked. How convenient.
Let me make a prediction: if you stand outside of the CIA headquarters with a camera attached to a laptop and some software that is doing license-plate scanning and face recognition, and – when the polite gentlemen in the black suburban arrive and throw you face down on the pavement – you tell them you were just exercising your constitutionally protected right to take photographs in a public place, you’ll learn that the CIA thinks facial recognition is a “search” if you do it to them, but not if they do it to you.
![Arizona Neo-Nazis [link]](https://freethoughtblogs.com/stderr/files/2017/03/arizona-neo-nazis.jpg)
Arizona Neo-Nazis [link]
The Government Accounting Office (GAO) has some harsh words regarding the FBI’s capabilities:[gao]
The Department of Justice’s (DOJ) Federal Bureau of Investigation (FBI) operates the Next Generation Identification-Interstate Photo System (NGI-IPS) — a face recognition service that allows law enforcement agencies to search a database of over 30 million photos to support criminal investigations. NGI-IPS users include the FBI and selected state and local law enforcement agencies, which can submit search requests to help identify an unknown person using, for example, a photo from a surveillance camera. When a state or local agency submits such a photo, NGI-IPS uses an automated process to return a list of 2 to 50 possible candidate photos from the database, depending on the user’s specification. As of December 2015, the FBI has agreements with 7 states to search NGI-IPS, and is working with more states to grant access. In addition to the NGI-IPS, the FBI has an internal unit called Facial Analysis, Comparison and Evaluation (FACE) Services that provides face recognition capabilities, among other things, to support active FBI investigations. FACE Services not only has access to NGI-IPS, but can search or request to search databases owned by the Departments of State and Defense and 16 states, which use their own face recognition systems. Biometric analysts manually review photos before returning at most the top 1 or 2 photos as investigative leads to FBI agents.
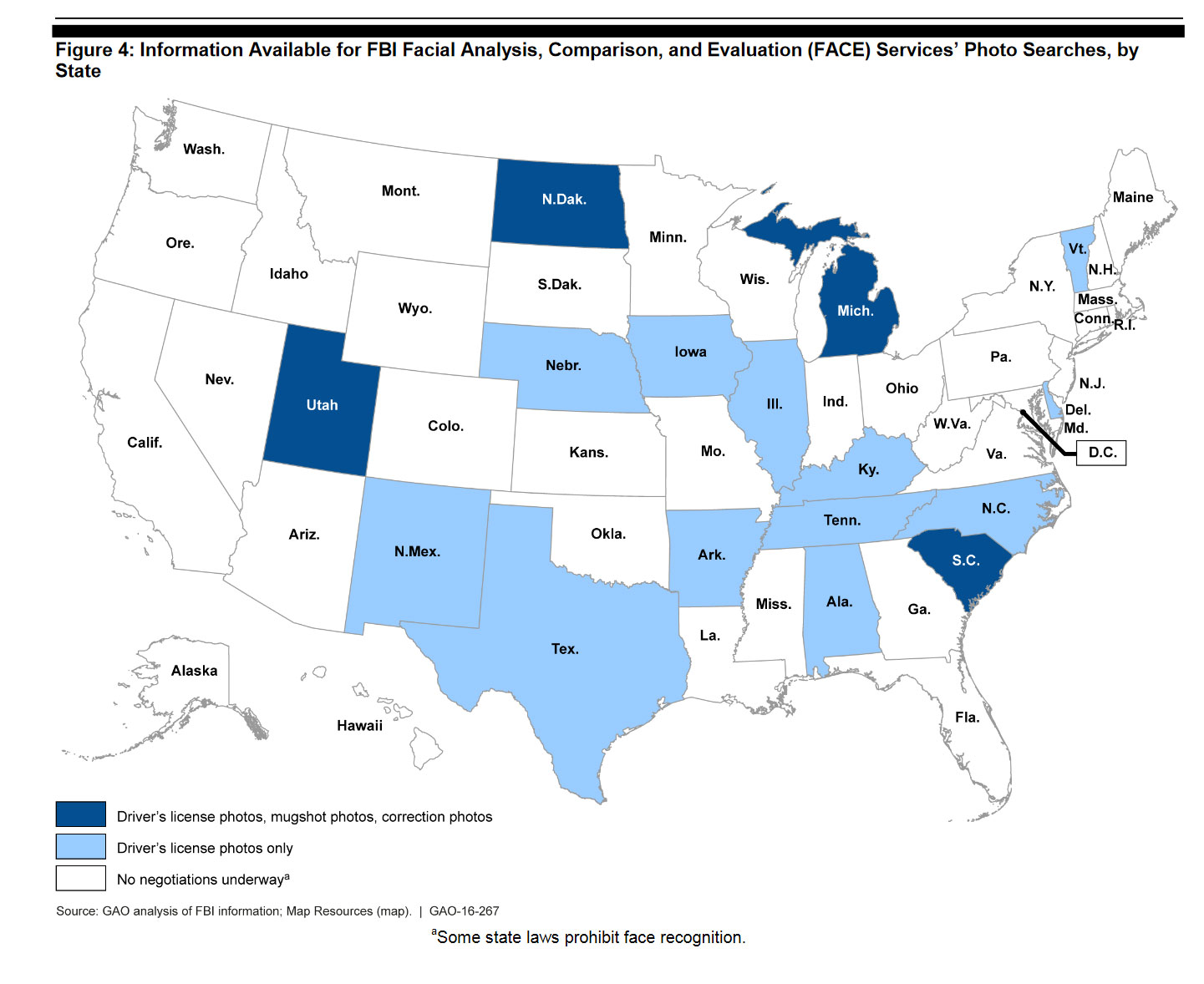
Face Time
As I have mentioned elsewhere, these databases have the problem that they’re not very secure against internal search. Pretty much all it takes is one cop – one member of the club who knows the secret handshake – out of hundreds of thousands of people – who’s willing to falsely request data. Go ahead and tell me that there are no cops that won’t search for that pretty young thing they saw go through security yesterday. Sure. Right. The problem isn’t just that this stuff is going into poorly secured databases, the problem is that it’s going to sit in Utah and never go away.
Prior to deploying NGI-IPS, the FBI conducted limited testing to evaluate whether face recognition searches returned matches to persons in the database (the detection rate) within a candidate list of 50, but has not assessed how often errors occur. FBI officials stated that they do not know, and have not tested, the detection rate for candidate list sizes smaller than 50, which users sometimes request from the FBI.
Let me wrap this up by telling you a depressing but true story. In 2011, I was an invited speaker at “New Trends in the Energy Sector” conference organized by QCERT in Doha, Qatar. It was a broad conference of many interests under the same roof, so there were physical security/state security/counter-terrorism, network security(me!), and plant management/resilience all in the same show. There was a large show floor, dominated by the state security/counter-terrorism crowd: lots of cool drones made of matte carbon fiber, cameras galore, that kind of thing. There was one thing there that blew me away: it was a Land Rover surveillance van. (OK, other than wondering “why didn’t they build it out of something more reliable, with a better electrical system?” it blew me away) Inside the van was a sort of cupola-thing, and two people could sit in the back. There were mini projectors projecting a multi-camera 360-degree view of the surroundings onto the interior of the cupola: you could sit back there and it looked like you were on the street, but you were at the height of the roof of the van; perfect for watching people walk by. There was a humming rack of computers (pull-out drive racks and a server) between the rear and the drivers’ compartment up front, but there was a flat panel that let you see the drivers as if you were there. As people walked by the van, the computers (which were projecting the video) were looking up faces; if someone was identified it would snap up a green box around them with their name and whatever information the computers had. You could tap on them (there was some kind of feedback touch sensor) and it would begin projecting the boxed person onto the driver’s windshield, like a heads-up display: “follow that suspect” and the driver would have a computer assist tracking them down the street or wherever they went – presumably it was matching colors as well as faces, maybe you could evade it by changing your shirt in a payphone booth. There was a video controller like an editing deck with a forward/backward scrubber; you could scroll back, pick a person, flag them so it would alert you if you saw them again, do a more in-depth search. You could walk by one of these things in the crowd outside the arrival hall of an airport, and it would look just like a convenience van for a luggage delivery service, or – whatever. In the US, of course, I’d wonder “who actually buys a Land Rover?” but in the US it’d be an econoline.
[source]
The reason the FBI and the police don’t really care whether their face recognition is accurate is: they don’t have to. They can grab you, throw you facedown on the concrete, and ask for your ID. If they didn’t shoot a few holes in you in the process you’ll be so happy you can walk away under your own power that you probably won’t do anything. As long as there is zero downside cost to law enforcement for making mistakes, they’re going to be completely unencumbered by concerns regarding getting your identity right. Good luck if you resemble someone wanted by the FBI.
Think how difficult this is going to be to elude, when you add in license plate scanner data and portable tracking device data. Did I say “portable tracking device”? Ooops. I meant ‘smart phone’ – but that’s a topic for another day. So is DNA. Do we even need to talk about those?


I had a surreal conversation at Interop back in 2012, when I bumped into Radia Perlman, who’s one of the circle of people I occasionally wind up at conference dinners and on panels with. I love Radia because she reveals me for the dummy that I am. Walking around with her, at one point we walked past a smallish network-attached storage array and someone (loudly, so we both heard it) said something about “it’d make a great porn stash!” and Radia got pensive for a minute and then, typically, smiled hugely and said, “I was just thinking: you know, at a certain point there was probably produced enough porn that nobody could watch it all in their lifetime. At which point it would have made sense – barring changes in fashion – to simply stop making any more. In fact we probably passed a point a few years ago where it’d be easier to just give it away and there’d be no market for it.” As is often the case with Radia’s casual observations, it turned out to be correct.
“How good do you think the protections are on that data, by the way”: when Snowden started dumping his NSA secrets, he appeared to be getting coaching from someone very media- and politically savvy. Initially, in fact, I was happy to hear some of Snowden’s comments sound remarkably like he had been reading classical anarchist arguments like Robert Paul Wolff’s – but then, the energy of the thing petered out, and he was on the run, and the smear machine got to smearing. I remember feeling elated because I thought we were about to see a brilliant strategy unfold, but it didn’t. What I hoped was going to happen was Snowden says: “there are all these programs in place” and the NSA’s liar-in-chief (someone like Clapper) says “no, there aren’t!” at which point Snowden throws down the NSA’s own slides. And then Snowden says “and there are all these other things…” and the NSA lies again. And Snowden throws down more stuff. I was fantasizing, I now realize, but I imagined that he end-game was that Snowden was politically sophisticated enough to throw down outlines of the NSA’s dumps on a couple of prominent Americans. Because, you know they have that stuff (to be fair, I assume there are ‘oligarch triggers’ that flag an alert if an analyst tries to access Jennifer Lawrence’s phone camera-roll) you can assume that there’s probably no protection on ordinary folks. In retrospect, Snowden’s disclosures only would have brought about change if he had dumped a bunch of the oligarchy’s personal data: Jeffrey Epstein’s texts, Nancy Pelosi’s emails, Kim Kardashian’s iPhone camera roll – stuff that matters.
By the way: if you do a google image search for “Marcus Ranum” be forewarned there’s a bunch of NSFW stuff. That’s deliberate. A bunch of years ago I decided to use my photography as a way of injecting a great deal of noise into some image classification algorithms. Does it matter? Probably not. I did it because I could.
A good piece on facial recognition from the Royal Society[rs]
I am told that gmail’s complete sender/recipient logs since the service began are about 100tb. And, of course they have them. Who’d delete something that delicious?
“How Convenient” – if US government were interested in, you know, right and wrong and rule of law, they wouldn’t go “look! a convenient gray area in the law! let’s exploit it!” they’d ask the supreme court for a decision, maybe air it publicly, and then act accordingly. The reason they don’t do that ought to be obvious: they know what the courts would say.
Emma Watson is a very interesting person, in terms of how much she “gets it” regarding her public interface. For example, she refuses to take selfies with fans, because she’s then geo-locating herself [cnn]:
For me, it’s the difference between being able to have a life and not,” Watson recently told Vanity Fair. “If someone takes a photograph of me and posts it, within two seconds they’ve created a marker of exactly where I am within 10 meters.”

Oh. This is sad, incredible, amazing, and sad. This is what a lot of money gets spent on. Wow. All those tweets… saved… like the stream of consciousness of a species. We could use that money to work on renewable energy but no, we’re saving tweets. And so many photos it’s astounding.
It answers a question I had at one time… Facebook would occasionally tell me that “my” photo had been commented on, or someone had “liked” it etc. It was not my photo. It didn’t even look like me. But apparently the computer thought it did. Now I understand.
The amount of porn (or other media for that matter) there is beyond your available time to watch it is only irrelevant if the porn is homogeneous or unfilterable. When you can filter it, the result is that with an increased amount of available porn your time can be filled with increasingly specific filters. The overall trend would be an asymptotic approach as filterable porn quantity increases towards a porn experience made to appeal to you specifically. (The same trend causes all sorts of problems when applied to proliferation of news media, but as far as I can tell its generally a good thing when it comes to porn.)
A remarkably informative post. Excellent!
—
Presumably, that very access also goes into the retroscope.
(One reason why though I trust each and every one of my cow-orkers, I still <Win>-L (lock) my workstation when I leave it unattended for any length of time.
—
[OT]
EveryZig, I figure that, as both CGI and AI improve, pr0n will become rendered on the fly and become more like a video-game. Actors just won’t cut it unless they’re elite.
This situation would be (slightly) more tolerable if this led to better law enforcement.
For example: There has been a whole lot of threats against Jewish community centres in the last few months. One person (a former writer for The Intercept, no less) has been charged with making eight threats, but that’s only a small fraction of alleged offences.
What gives? If ANY of this was about making the community safer, how can this go on for month after month?
polishsalami, thus ‘retroscope’.
(It’s reactive, not proactive)
[meta]
… or, not the Panopticon.
(Yet)
Take heart! All of this shit is largely for naught!
I am reading this *fascinating* book about an early french revolution, and an almost throwaway remark caught my eye. This particular revolution, as indeed I realized all revolutions are, was carried out in a very public manner. People did not communicate with secret notes, they printed pamphlets and papered Paris with them. Secrecy occurs in the early parts of revolutions, while the incompetent goobers sit around having Sekrit Meetings and shit, sure, but none of that matters. What matters is when the few marginally competent people (i.e. the fascist bastards) get behind the thing and start whipping up the mob. Then the bad guys are too busy screaming into the radio for backup to do any facial recognition, and anyways everyone knows that asshole waving his arms around is a guy named Josef already.
So what IS all this shit for? Mostly I am convinced that it’s sheer fetish. Bureaucrats have some weird idea that if they just have sufficiently massive files, then something good will occur.
Yes, it’s used extensively for low-level harassment. It’s used for political hatchet jobs. It is NOT used to solve ordinary crimes (blah blah parallel construction is hard and not worth it most of the time etc). It constitutes a pain in the ass for the citizenry, and from time to time, produces more or less random horrific outcomes.
kestrel@#1:
Facebook would occasionally tell me that “my” photo had been commented on, or someone had “liked” it etc. It was not my photo. It didn’t even look like me. But apparently the computer thought it did. Now I understand.
Yeah – something tagged someone in a picture as you. It’s also a trick used by marketing/advertising for a while: you post an ad then tag the person in the picture as someone: they get the notification and click on it, then see the ad. Such an important message!
I see that sort of stuff as very good because it helps keep the system noisy and unreliable.
John Morales@#3:
Presumably, that very access also goes into the retroscope
Ideally. One hopes. Maybe.
It depends on whether the system keeps inner access logs and whether those are folded into the systems’ own logs or not. Usually, I’d say that’s not the case, which is why you have things like the CIA not knowing what Aldrich Ames took, or the NSA not knowing what Snowden took(they probably have a pretty good idea by now, but little birds have told me there was “one hell of a fire-drill”) or State didn’t know what Manning took.
Back in 1998 or so, Marv Shaeffer from Arca and I got looped into doing some security assessment on the IRS’ “CyberFile” system and wrote a scathing report recommending that it not go online in its then-extant configuration. One reason: there was absolutely no retention of information about who queried what, once you got past the original web front end. The entire system was built around the assumption that the officially-supported access path was the only one that anyone would choose. That’s dumb as mud but it’s a fairly typical assumption I’ve found in many places. For example, Snowden (details are thin about what happened) appears to have used some kind of “grazer” against a number of internal systems that supported a web interface. The security model was “once you’re inside, you’re OK” more or less, so Snowden’s accesses were bypassing the official access path (allegedly one of his co workers did ask him why he was accessing so much stuff and allegedly he explained that he was setting up a backup/restore process)
John Morales@#5:
It’s reactive, not proactive
That’s a key point: none of this stuff gives anyone enough information to predict the future. For obvious reasons, that’s still a hard problem. So, all of this stuff (at best) is useful for retaliation.
To the question that was asked on my previous posting on this topic: “what do we do about it?” that’s one answer: to defend ourselves against this kind of system we must be willing to not give a fuck, or (if we want to survive to fight another day) be creative and keep coming up with things they haven’t thought of. If the FBI is looking for people buying tannerite and pressure cookers, we’ve got to buy black powder and fire extinguishers. Oh, oops, did I say that? Better think of something else.
Andrew Molitor@#7:
This particular revolution, as indeed I realized all revolutions are, was carried out in a very public manner. People did not communicate with secret notes, they printed pamphlets and papered Paris with them. Secrecy occurs in the early parts of revolutions, while the incompetent goobers sit around having Sekrit Meetings and shit, sure, but none of that matters.
Yes! One of the things that drives me moderately nuts about my fellow armchair revolutionaries is that we don’t study revolutions in the past.
The same could be observed Re: the American revolution. Something like 80% of the population read (or heard read) Thomas Paine’s “Common Sense”* It was hugely popular and stimulated a level of discourse that is similar to today’s discourse around Trump. Everyone was going back and forth about it – it didn’t necessarily start the revolution, but it framed the discussion for it, much as Voltaire’s anti-authoritarianism framed the discussion that the Jacobins continued.
(* According to one of the interviewers on the BBC “in our times” episode on Paine)
Andrew Molitor:
So what IS all this shit for? Mostly I am convinced that it’s sheer fetish. Bureaucrats have some weird idea that if they just have sufficiently massive files, then something good will occur.
Quoted for truth.
Exactly. Mandela did not evade the security services. Ghandi did not win Indian independence from the shadows. MLK did not hide from the FBI.
People achieve shit because they’re willing to stand up for it in public. Willing to go to jail for it. Willing wait patiently in line to be beaten senseless by the colonial police for it. Maybe even willing to die for it. Yes, the security services are oppressive, and they’re going to surveil everyone, and keep yottabytes of data on everything – and that is exactly what a successful revolutionary would use against them.
Andrew Molitor @ # 7: … this *fascinating* book about an early french revolution…
Damnit, quit that teasing! Author and title, or it didn’t happen!
I can’t imagine the French Revolution took place without any secret notes and bags of silver changing hands late at night – c’mon, we’re talking about Paris! L’ancien Regime! all that Marie-Antoinette porn didn’t print itself! – but I doubt those actions did more than slightly accelerate the inevitable.
Of course, afterwards, the exiled aristos needed a scapegoat and chose the bourgeois-Jesuit mutual-promotion society known as the Illuminati of Bavaria, which (a) excused them from examining their own crimes and clumsinesses and (b) provided a boogeyperson for two-and-a-quarter centuries and counting of konspiracy kooks to ramble on about and the rest of us to identify them by, so we owe them at least a half-bow.
I am being coy, it is in fact a book written by Ranum Senior. “The Fronde” by Orest Ranum, and it’s very interesting to me within the current political climate. I am using it as a Handy Primer for thinking about how close we are right now to an actual revolution, and then answer, surprisingly, is not very close. Shit gets a whole lot sketchier before the knives really come out.
Andrew Molitor @ # 15: “The Fronde” by Orest Ranum…
One more for the “look for” list – thanks!
Shit gets a whole lot sketchier before the knives really come out.
Yabbut that was mostly nobles vs. le roi, with the proto-fascist element firmly under the archbishops’ thumbs. Things do tend to move faster here in The! 21st! Century!!!
What’s surprising about it? It usually takes masses of people starving to death in the streets, and even then it’s nowhere near guaranteed. Political liberties and civil rights are luxuries that most people will happily live without in a pinch, as long as they’ve got food in their bellies. And rightly so – revolution is a crapshoot at best, and is always a hideously messy and dangerous business.
Dunc @ # 17: … masses of people starving to death in the streets…
Most of the truly hungry in France of 1789 lived in the countryside. Likewise for the Russians of 1917. Spartacus didn’t need a famine to rouse the Roman rabble 2, 090 years ago either.
And the volunteers answering the respective calls of G. Washington and S. Bolivar generally ate better at home than in the army.
Several historians have claimed that neither absolute nor relative deprivation sparks revolts – but the rulers need to watch their butts whenever conditions for the masses improve enough for them to feel hope but not fast enough to avert them feeling frustration. (I haven’t seen anything on that topic in a decade or longer, so perhaps that conclusion has been superseded…)
Pierce R. Butler@#16: and Andrew Molitor@#15:
Oddly, I just queued a bit on the Fronde to drop thursday.
I can’t imagine the French Revolution took place without any secret notes and bags of silver changing hands late at night
Actually, it happened extremely openly! It’d be a pretty easy argument to make that most popular revolutions shouldn’t be surprises – probably the quintessential popular revolutions that resulted in non-dictatorship would be Poland in 1980-90, Hungary, and Romania in the 90s. Like the revolution in France, they were slow-moving disasters for their rulers.
Marcus Ranum @ # 19: … it happened extremely openly!
Well, most of it happened that way, enough not to leave any major causative questions open. But –
I think we still don’t know just who spoke with the Duc d’Orleans when decided to oppose his royal cousin and rename himself Philippe Egalité; or what whisperings went on in the former monastery which had become the Jacobin Club; or who furnished the jewels for Danton to bribe the Duke of Brunswick to march his army elsewhere (or whatever happened that fateful night); or whoever ran off with the poor Dauphin; or …
As for open revolutions, that too comes down to viewpoint (does anybody have any doubts that a particular Agency in Langley, VA, helped those proud Polish patriots along?). I happened to be in Tehran a year or so before the lid blew off, and could tell tensions were rising (lots of people wanted to practice their English with me – until I mentioned politics, at which point they all suddenly heard their mamas calling), and probably felt much less surprise when the balloon went up there than did, say, the Shahanshah and his friends in a certain spook-rich Embassy.
Pierce, @18: You’re probably right – I had had several beers when I posted that, and it’s a bit glib in retrospect.
“Control can never be a means to any practical end other than more control.”
I was in a bar in a ski resort this time last year. At the next table was a member of the British royal family. One of our party went over and asked for a selfie with them. It was graciously and regretfully refused, and now I have another reason why that might have been.
(Aside: the party consisted of said royal personage, one female friend about their age, one male friend about their age… and one dude in (I estimate) his early fifties, a lean, fit-looking chap clearly not related to any of them. I still wonder what he was equipped with.)