Other than “don’t use the internet”* the best thing you can do is: your backups. I’ve covered that elsewhere. The second best thing you can do is to get out of the password business. The third best thing you can do is segregate some of your computing.

Robert Morris Sr. Former NSA Chief Scientist (Marcus Ranum photo, circa 1994)
Today, let’s talk passwords. First off, passwords are a really bad idea. They only ever made sense on un-networked time-sharing machines, back around 1960-1975. The game with passwords was over by 1980, and Dan Farmer and Alec Muffett hammered the last nail in that technology’s coffin by 1990. But then, zombie-like, passwords had a resurgence of life thanks to Secure Socket Layer (SSL) – which is actually neither secure, nor sockets, nor a layer – which is very widely used to exchange reusable passwords over encrypted links, from unsecured desktop systems to moderately secure websites. Robert Morris Sr once described this as “using an armored car to deliver a paper bag of money to a guy living on a park bench.”
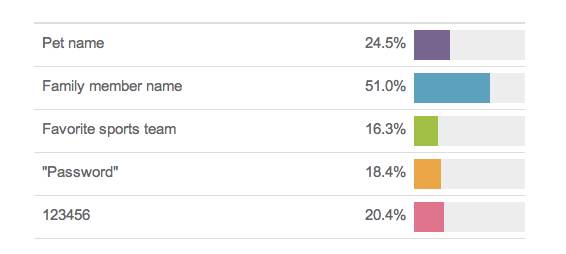
The problem with passwords, other than that they can be intercepted in transit and re-used, is that they can be attacked offline. If you can get a file of password hashes from a website (which can be remarkably easy) you fire up a few computers running Crack and pretty soon unencrypted passwords will start falling out. By the way, 123456 is the most popular password; don’t use that. Use 00000000 like the US Government used to use on the “football” with the nuclear launch commands, and in minuteman silos during MacNamara’s stint as Secretary of Defense.**
Suppose your Yahoo! account was compromised 2 years ago and they just got around to telling you. Well, during that 2 years, if your password was crack-able, it was lunchmeat for hackers. And if someone wanted to get into your account, they could have. And if you used that password for lots of places: Yahoo! Google, and Freethought Blogs, Amazon.com and Ebay – now your other accounts are compromised, too. That’s a fairly common hack paradigm, by the way: when they break into some piddly webforum and crack its passwords, something like 20% of the users also used that password for Amazon.com and Ebay. Boom!
Don’t do that.

From the sourcefire 2004 calendar (concept and design by Marcus Ranum)
A lot of security people say “don’t write your passwords down” but that’s manifestly false. You’re actually much safer if you have a big sheet of paper on your desk with all your passwords – as long as they’re long and random – because it’s hard to steal the paper over the internet. (although I did see one guy hack a webcam in a data center and there, on the console…. post-it note!)
The best thing you can do right now is not use the same password everywhere. Which means install a password safe, generate large random passwords, and you just use copy/paste to paste them into password fields. I have, literally, not remembered a password for years. Because my passwords are too gnarly to remember, and I have about 50 entries in my password vault, and none of them are the same. Here’s my old password for FreethoughtBlogs:
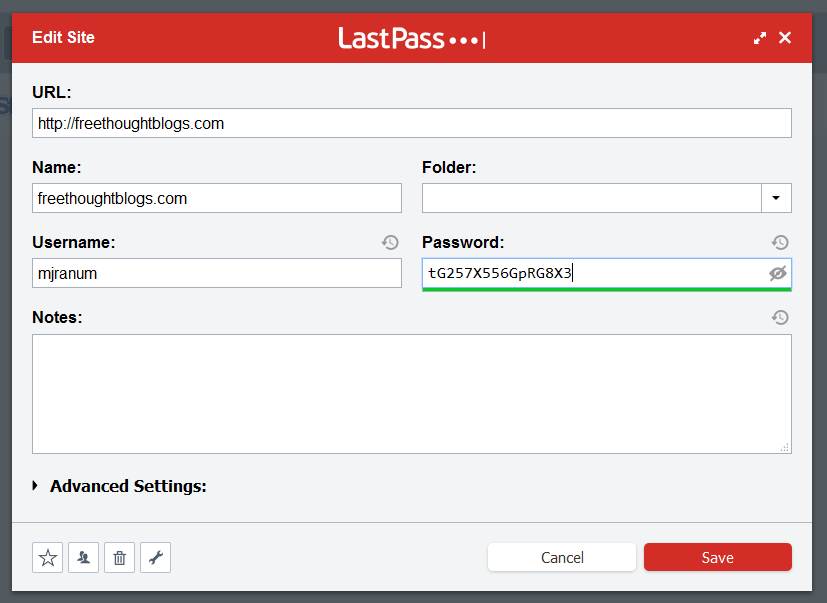 Lastpass has had some security problems in the past. Which is annoying as hell. For that reason many of my friends use offline password vaults – it’s only on their iPhone not in the cloud,*** which means they can’t copy/paste. Anyhow, I use Lastpass and take advantage of their cloud synchronization, so all my passwords (and they are seriously long and gnarly) are accessible on one desktop and my phone.
Lastpass has had some security problems in the past. Which is annoying as hell. For that reason many of my friends use offline password vaults – it’s only on their iPhone not in the cloud,*** which means they can’t copy/paste. Anyhow, I use Lastpass and take advantage of their cloud synchronization, so all my passwords (and they are seriously long and gnarly) are accessible on one desktop and my phone.
Here’s how you use a password vault:
- Install the vault
- Pick an insanely great passphrase for the vault. My old one was: “The C0nstipation of O’Brian” Make it long, easy to remember, and throw typos in, as a sacrifice to Ytpos, the god of internet bloggers. When the CIA starts waterboarding you for your password vault’s passphrase, you’d better hope it’s not “I will never tell you ever ever!”
- Go to all your favorite websites and forget your password, do the “password reset” login, get the email go to the screen, generate a random password, and move on to the next. Total time will be about an hour. Go in order of descending importance.
- Turn off your browser’s tendency to helpfully remember passwords except for on sites you genuinely do not care about at all. Remember, now, if one of your site passwords gets compromised, they haven’t got all your sites
- Turn off all attempts to “link accounts” between things like Twitter, Facebook, or Ebay and Paypal. Those are just like delicious candy for hackers.
- Your password resetting in-box is a critical component of your security, now – ideally it should be something hard to get at (for example, if your accounts were all tied to mjr@yahoo.com, then all a hacker’d have to do is use your compromised yahoo.com email address to reset all your other passwords and shazam, they are you!)
If you’re using a site that has an option to use something like google authenticate, or a smart phone authenticate, or an SMS text authentication: USE IT. There are always plenty of security folks who will complain about theoretical man in the middle attacks against the SMS system … Sure, but: passwords are the alternative and they are a lot worse.
I’m going to end by telling you a horrible but true story. So, on a sunday morning one day, my phone rings and it’s a guy who sounds very upset. He tells me that [so-and-so] recommended he call me because he needs security consulting help/incident response/expert witness – the whole bit. Eventually I get the story out of him: he woke up that morning and checked his portfolio on his online trading account and his $400,000 worth of IBM stock, which was his retirement, had turned into $12,000 or so of some penny stock. We talked a lot and the story unfurled further: he’d used to use Fidelity Online but didn’t like their fees and had switched to a cheaper trading service, his home computer was shared with his family and one of his kids**** had gotten into some malware and a keylogger was installed and the hackers got his password for his trading account and used his IBM shares in a “pump and dump” for a penny stock. Then, I carefully read the end user license agreement from his discount online stock trading service, and had to tell him that, in my professional opinion, he’d never see his $400,000 again: the service said clearly that it was the user’s responsibility to ensure the security of their credentials, blah blah, but, yeah, sorry. He called me some nasty things, but was good enough to call me back a couple days later and apologize. I didn’t charge him for my time. He’d spent enough money lately.

In that guy’s case, a password vault would not have helped him. What would? 2 factor authentication: something you have plus something you know. Technically, someone like me who’s using a password vault on a dedicated system is using something like 1.9 factor authentication. ;)
For someone like him, the best thing to do (I used to do this for a certain project) is to go on Ebay and buy an older laptop, or a new iPad or something like that, and use it as a dedicated terminal for that single purpose. Have your “trading iPad” that is, basically, a password vault, print your password out and store it in your safe, and store the 20-character random password in your trading iPad’s memory. Then don’t use it for anything else, most particularly not email or browsing. The poor guy I talked to lost $400,000 in order to save $15/month because the trading service that offered some liability protection was too expensive. If you’re talking about your entire net worth being in one place, $400 for an iPad mini as a trading device is chump change. If you go the route of using a windows laptop, make sure you use AppLocker so the only thing it can run is a browser, then punch rules into Windows firewall so that the only place it can browse to is the online brokerage.

(* That is a serious option)
(** I would not make up something that ridiculous. Here’s an overview)
(*** Well, it’s also in the iCloud and probably iTunes backup and …)
(**** I did not say “Yeah, Right” but I thought it.)
(***** How many sports team names are there? How long does it take a GPU to test them all against a hash?)

I use a USB hostless modem for my internet, which is pre-paid (I usually top up with $30 or $50 vouchers). A few months ago, my data credit started leaking away; putting this down to Windows updates, I topped up with $30 of credit (3GB), but that soon disappeared.
After some panicked calls to the company’s service centre, I topped up again — same problem. This led me to approach the company in person. They could find nothing, and suggested a new SIM card, and that I change all my passwords. I managed to explain the situation to the call centre, and they were good enough to give me 2GB back, but I still lost about $45 worth.
I still haven’t been able to find any viruses etc. or any evidence that my device has been compromised. I haven’t had any data drains since. The best explanation I (a computer novice, basically) have come up with is that I may have done something to trigger the download of Windows 10, but given that I still have my old system that doesn’t seem right.
https://youtu.be/a6iW-8xPw3k
That’s a scene from Spaceballs, BTW.
polishsalami@#1:
It probably was not an attack. They tend to look for stuff they can convert to money or cash equivalent. If someone was reselling your bandwidth it would have been drained very fast.