If you haven’t seen the Talking Heads True Stories you should. [amazon] But that’s not what we’re going to be talking about today. I just needed a title for the blog posting, and that got me thinking.
I love the scene where the revival preacher does “Puzzling Evidence” which might make good theme music for you to listen to while you read the rest of this.
There’s a few security people doing detailed forensic analysis on “Guccifer 2.0″s DNC file-drops. I’m glad to see that’s going on, because there’s always a tremendous amount of information stored in any computerized action, and to understand the action, we can determine if the meta-information is consistent.
Analysts looking at embedded time-stamps in documents and in the archives that were dropped are coming to all kinds of interesting conclusions. For example, according to the analysis, some of the documents were created ~30 minutes before they were copied, based on creation date/time and creator information embedded in the document by Microsoft Word. The analysts then look through file dates in the .ZIP files and match them. You can learn a lot from discrepancies there, as well as deltas between file creation dates in the filesystem and embedded creation dates. There’s a great deal of detail and, honestly, I’m not sure how much of it is spurious and how much is not – however there’s a small but enthusiastic community that believe Guccifer2.0 probably was “inside” with a USB stick, rather than coming in from the internet from wherever else he was claimed to be coming from.
The problem with conspiracy theories is that you take your facts and back-fit a story that covers them and makes sense, sometimes omitting facts that contradict the story. To tell if you’re looking at a good theory, or a bunch of motivated reasoning, you have to do your own analysis of all the available facts, then build your own theory and match it against the other stories. It’s a huge amount of work, and it’s not particularly rewarding.
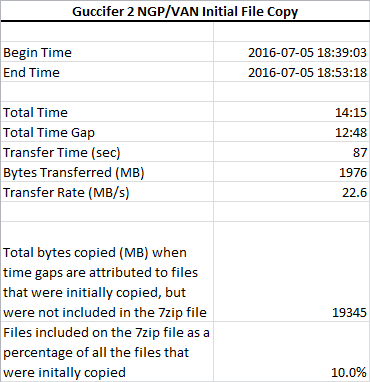
This is interesting: [forensicator]
- On 7/5/2016 at approximately 6:45 PM Eastern time, someone copied the data that eventually appears on the “NGP VAN” 7zip file (the subject of this analysis). This 7zip file was published by a persona named Guccifer 2, two months later on September 13, 2016.
- Due to the estimated speed of transfer (23 MB/s) calculated in this study, it is unlikely that this initial data transfer could have been done remotely over the Internet.
- The initial copying activity was likely done from a computer system that had direct access to the data. By “direct access” we mean that the individual who was collecting the data either had physical access to the computer where the data was stored, or the data was copied over a local high speed network (LAN).
- They may have copied a much larger collection of data than the data present in the NGP VAN 7zip. This larger collection of data may have been as large as 19 GB. In that scenario the NGP VAN 7zip file represents only 1/10th of the total amount of material taken.
- This initial copying activity was done on a system where Eastern Daylight Time (EDT) settings were in force. Most likely, the computer used to initially copy the data was located somewhere on the East Coast.
- The data was likely initially copied to a computer running Linux, because the file last modified times all reflect the apparent time of the copy and this is a characteristic of the the Linux ‘cp’ command (using default options).
The “speed of transfer” calculation is interesting: it was arrived at by looking at the deltas between the creation times of all the files in the archive, then working backwards to measure the bandwidth used. If I copy 100 files of 100mb each that’s 10gb and if the first copy was completed at exactly midnight and the last copy operation completed at 12:00:10, then I copied 1gb in 10 seconds so my bandwidth used was 100mb/sec.
[source]
It’s an interesting theory but I’m still not convinced, mostly because it raises more questions than it answers, and I don’t want to take the time to dig out the answers. For example, one popular technique hackers use is to snatch copies of a target’s data to a local archive, compress it, and exfiltrate the archive. In that case, the creation of the local archive is going to be at high bandwidth relative to the internet. Some of that sort of activity might be consistent with the presence of a PWN Plug.

[source]

Disclaimer: I am not saying that there is a PWN Plug in DNC headquarters; the fine makers of PWNie Express disclaim etc, etc. But if I were trying to hack opposition computers I would not bullshit around with unreliable internet connections and waste my time proxying my traffic from Russian sites so that they’d find me in the retro-scope: I’d send in “the plumbers” [wikipedia] to gift their offices with a new power strip. You know, sort of like the Nixon team did? When they broke into the DNC offices in the Watergate? Yeah, like that.
That still doesn’t mean it’s the Russians! Or the CIA! Or that it’s not the Russians. Or the CIA. If you are comfortable that the hackers sign their work using Russian fonts and a very Russian name, by all means remain comfortable. I’d be appalled if the Russians’ tradecraft were so mediocre, but maybe it’s deliberate – they pretty much signed the Litvinenko murder – maybe this is tradecraft within tradecraft or the tradecraft of no tradecraft.
[source]
The recent release of emails from Donald “Sun Tzu Jr” Trump Jr certainly does a lot to point the finger at Russia. As I’ve said before, I’m quite comfortable with the idea that Russians are behind manipulations of the US election, along with the Democratic Party, Republican Party, Koch Brothers, and everybody else. My main concern, as a computer security professional, is that my field has become another battleground of sloppy propaganda. Ignorant talking heads on television talk about “government agencies say this” and “sources and methods” and all it does is makes me wonder whether every other professional field is being mis-reported as badly. I know what happens, because I’ve done it: you get a call from some news agency and they want to ask about Russian hacking, so you agree to go on record:
Interviewer: “Was it the Russians?”
You: “Well, it’s complicated. Maybe. Let me explain…”
Interviewer: “Uh, huh, thank you.”
Then later you see that they found some wild-eyed stooge who believes everything, who’s ranting, “OH, yeah, that’s how they do it!” I’ve done dozens of interviews that I’ve never appeared in, because I’m trying to actually be technically accurate, so I wind up on the cutting room floor.

In the video, the preacher asks “Do you know what Bobby Ray Inman was doing before …” and says Inman was running the CIA. I’m impressed that David Byrne even knew that name! Inman was director of NSA (DIRNSA) and assistant DCI, before he retired to the ex-government gravy train and was involved with a contractor that was exporting nuclear technology to South Africa and Iran. Whups.
One of the characteristics of the Talking Heads’ work is the way they divert into seemingly random side-themes. I do that a lot in my writing. Whether that’s a good thing, or not, it’s a thing and I wonder to what degree I’ve been influenced subconsciously by surrealist artists, or maybe I’m just scatter-brained. It makes me happy when I see it, because it mirrors how I think: there’s a whole lot of irrelevant stuff always going on in my head and sometimes it bubbles up and out. Someone who obsessively tries to link those bubbles into a coherent world-view might be a “conspiracy theorist.”

Source: museum of american history
23mb/s isn’t that big a deal anymore. Especially not if you’re in Verizon’s FIOS cloud. Up here where I have metered bandwidth WiFi I get 10mb/s. I think the analysis is interesting, but I don’t accept their conclusions; time will tell. While I was checking to see the location of the DNC headquarters (to check bandwidth options) I stumbled across a really funny picture: wow, those ex-CIA spies were pretty damn subtle in those days! I literally laughed out loud when I saw that. Look at the lock: I have taught 12-year-olds how to pick locks like that. I’m old and slow now but I’d have had that thing open in under 2 minutes. How exquisitely stupid!
Tradecraft of no tradecraft – a friend of mine says he’s pretty sure there were multiple teams moving through the DNC’s systems at more or less the same time. That’d make it confusing: imagine if there was an insider exfiltrating stuff on a USB stick and a network-connected insider using a PWN Plug. And (per SOP) one of the staffers works for China and another works for the RNC. The most obvious tradecraft of all is to have one of your people working for the opposition – that way they can screw things up or report as events play out. Perhaps Donald Trump Jr is a DNC plant, and Debbie Wasserman Schultz is an RNC double agent. That would explain some of the mind-bending WTF we’re experiencing.

We have a similar filing cabinet.
If you tilt it back, you can shove the lock-bar up with one finger.
.
Back in the days of floppy discs, the boss locked the storage box and took the key on vacation with him.
We jimmied it open with a kitchen knife in under a minute.
chigau@#1:
If you tilt it back, you can shove the lock-bar up with one finger.
That’s way too subtle for the CIA. I’m surprised they didn’t use explosives.
Richard Feynman used to tell some really funny stories about the filing cabinets at Los Alamos. Hm. I should do a posting on some of that some day.