I thought they were ugly, stupid, and pointless a few years ago, but apparently, there’s still a market for them.
Wait until they realize they don’t own them after all — they all belong to Amazon, and when Amazon sneezes, the bored apes all curl up and die.
Amazon owns everything, and the recent loss of service also meant that the Canvas application we use for teaching was having seizures, too. Fortunately, I wasn’t teaching this term, and even if I was, I go to class with all my teaching stuff stored locally on my laptop. Because I’m not a dumbass.


Bored apes fell for a silly fad. The technology it uses is interesting, though, and occasionally useful.
The block chain? I’ll admit it’s “interesting,” but I don’t see where it’s useful.
Yeah the block chain continues to fail to find a use outside of speculative “currency” or the NFTs. a lot of it comes down to the promises not living up to the realities of the problems they are claiming to solve (smart contracts seem dumber than just regular contracts, I am not storing medical information on the block chain, no company worth its salt is going to put its distribution network on a public resource they can’t control, and for what it is worth, using a block chain for any of that is more costly than the solutions that already exist and work exceedingly well…)
As to the PZ’s comment on Canvas, that’s nice but us remote and online students don’t necessarily have the luxury of flying to the college campus where our classes our taught IRL and attending classes. It’s not just about being smart or dumb…
@3 RR Rabbit
Append-only data structures have additional uses outside “The block chain”.
soatok (dot) blog /2024/06/06/towards-federated-key-transparency
soatok (dot) blog /2024/08/21/federated-key-transparency-project-update
Soatok describes a protocol they’re working on for end-to-end-encrypted private messages in the Fediverse (Mastodon, etc.) They seem to know what they’re doing.
@3 killyosaur
I wouldn’t store it there either, but consider this: unless you’re storing that info yourself, what makes you think it’s being stored securely at all? Medical info notoriously has to be handed around to dozens of private third parties, few of which are interested in crypto beyond legal requirements. Chances are, they met HIPAA compliance by encrypting your medical info and storing the key unencrypted in the database for easy retrieval, which means anyone with access to the database can also decrypt it.
If you want to save your money safely, instead of NFTs I can look after your gold bars and Krugerrand for you.
The bible says money is bad, so I will store the gold in my special “Evil begone” vault.
Append-only data structures, yeah, I suppose that’s worthwhile. As you were.
lol @birgerjohansson
my Krugerrands are on their way to you.
https://criptonav.com/nft-use-cases-2025/
Not at all a computer acrobat, but I know no one who is using blockchain at work. AI has been eagerly adopted by some colleagues (particularly those in data/image analysis), not so blockchain-related applications. But then my field of view is woefully limited.
NFTs on the other hand… here’s a good presentation in four panels:
https://www.toonhoundstudios.com/comic/20220131/?sid=372
as I understand it, they are mostly curiosities now, of very little value.
outis, your understanding is behind the times.
cf. https://lawlibrarianship.com/the-legal-status-of-smart-contracts/
It’s not like “the blockchain” invented append-only data structures. At all.
“The blockchain” is specifically an intensely inefficient and slow way to implement an append-only spreadsheet which is built around the singular feature of basing most of the important security guarantees off of wasting electricity.
What I’m saying is that it’s neither interesting nor useful.
Elladan, in what manner do you think it’s an intensely inefficient and slow way to implement an append-only spreadsheet which is built around the singular feature of basing most of the important security guarantees off of wasting electricity.
It’s not a like-for-like replacement to a ledger, it’s got other properties.
“What is Blockchain?
At its core, blockchain is a digital ledger that records transactions across many computers so that the information recorded cannot be altered retroactively. Think of it like a digital notebook where every page (or block) is connected to the next one, forming a chain. Once something is written on a page, it can’t be erased or changed without affecting all the subsequent pages. This structure, often described as a decentralized and distributed database, ensures that data remains secure and trustworthy.”
(https://blockchainmagazine.com/learn/what-is-blockchain-explained-in-simple-words/)
Care to dispute any of that?
……unless you’re storing that info yourself, what makes you think it’s being stored securely at all?
I could ask the same of this new blockchain stuff; especially after seeing libertarians bragging about how Bitcoin movements were totally untraceable by governments, and then government(s) bust a crime gang by tracing their Bitcoin movements.
Raging Bee@14–
From the very start, cryptobros insisted that (1) blockchain transactions were untraceable due to encryption and (2) ownership can be proved with the blockchain. Both statements cannot be true at the same time.
As it turns out, criminal investigators have traced blockchain transactions and cryptocurrency stashes have been stolen. So in fact neither is true.
Raging Bee, you are over-simplifying.
Blockchain’s security comes from its decentralised structure: since data is stored across a network of independent nodes, and only verified by consensus from the majority.
Again: each block is cryptographically linked to the previous one, so tampering with any record would break the entire chain and be immediately detectable by all recipients.
Obs, it’s not magic.
The primary vulnerability in blockchain systems is where a majority of the networks collude with modified data. cf. https://www.dci.mit.edu/projects/51-percent-attacks
chrislawson, exactly.
By nature, the chain is distributed and public. The more participants, the harder for that 51% attack.
Blockchain’s security comes from its decentralised structure: since data is stored across a network of independent nodes, and only verified by consensus from the majority.
Yeah, but sometimes there’s instances where “the majority” are split, because some people’s nodes disagree with others’ about the validity of certain transactions.
Um. The majority cannot even in principle be ‘split’, given it’s by definition more than half.
The specific case at hand (from https://dl.acm.org/doi/fullHtml/10.1145/3407230) is:
“3.1.1 Consensus Mechanism Manipulation. Blockchain consensus mechanisms such as proof-of-work or proof-of-stake have been subject to attacks [38]. The 51% attack is a well-known attack on proof-of-work blockchains whereby an attacker who controls the majority of the network’s computing resources is able to discard blocks mined by anyone else, giving priority to his own blocks. Note that this attack does not allow an attacker to craft fake transactions or create money out of thin air. It will, however let them perform double spending. In practice, such attacks are extremely costly on blockchain networks with high hashing rates [23], such as Bitcoin, and therefore, quite rare. One possible prevention technique is to perform formal verification [61] of the consensus mechanism.”
First, yeah, that’s why I put “the majority” in “quotes.”
And second, your quote does not refute my claim.
I think it does address your point.
If consensus requires more than 50% agreement, how can that majority be meaningfully ‘split’?
(Doesn’t that contradict the definition of consensus in this context?)
Because you can have a three or four way split and then it takes a lot of wasted power to claw back to majority and somebody can be double-spending until the network does claw back. 51% attack is not the only attack possible.
No.
Good grief!
Holding more than 50% of the total vote or share is, by definition, a majority.
By definition this is a binary threshold: exceeds 50%, or it does not.
I think you (and others) are analogising to politics, but that is not the case.
Either a new entry is validated by consensus (majority), or it is not.
What part of “The primary vulnerability in blockchain systems” was confusing to you?
It’s the only structural flaw.
(Hint within my adduced quotation: “3.1.1 Consensus Mechanism Manipulation. Blockchain consensus mechanisms such as proof-of-work or proof-of-stake have been subject to attacks [38].)
“Either a new entry is validated by consensus (majority), or it is not.”
Correct. And by the time it is, a malicious person (or three) could do all sorts of fun things. That’s the point.
Either a new entry is validated by consensus (majority), or it is not.
True; but if it’s NOT validated by a majority, or if the opposing minority is significant (i.e., maybe 33% or higher, as opposed to a tiny faction of assholes or malcontents), then there’s a problem.
No. You are not listening. Nor checking stuff.
You are disputing out of ignorance, mathematical and linguistic.
A majority means more than half; a plurality means more than any other.
It’s the former, not the latter.
cf. https://hacken.io/discover/51-percent-attack/
↓
“What Is A 51% Attack?
A 51% attack is an attack on a blockchain network where a single entity gains control of more than half (51%) of its staking or computational power. This disproportionate control allows them to implement substantial changes, contravening the decentralization principle fundamental to the blockchain. In other words, a 51% attack gives the power to rewrite tx history, prevent tx completion, stop rewards to validators, and double spend.”
—
More than half the computational resources of every other entity on the system, eh?
It’s not exactly trivial, and you clearly appreciate not its scale.
More than everyone else, not more than the next largest grouping.
(Was it not you who was among those who railed about the required resources to run these things?)
[grr. bad expression, embarrassing; fix follows]
… more than half of the total computational power of the entire network, but rather the sum of all others combined.
You are not listening, John.
Which part of : “51% attack is not the only attack possible.” is unclear here? You’re talking about 51% attack but I am not talking only about 51% attack.
again, this time without the useless emphasis, given that you missed it.
“(Hint within my adduced quotation: “3.1.1 Consensus Mechanism Manipulation. Blockchain consensus mechanisms such as proof-of-work or proof-of-stake have been subject to attacks [38].)”
Had you looked, you’d have noted ‘3 KNOWN VULNERABILITIES’.
Of those, 3.1.1 is the one I mentioned as foundational and intrinsic, because the others are driven by procedure or technique, not by process.
So, had you looked, 3.1.2 Underlying Cryptosystem Vulnerabilities, 3.1.3 Improper Blockchain Magic Validation, […], 3.1.6 Public-key and Address Mismatch would have been visible.
Yes, other vulnerabilities.
But they are implementation problems, whereas only the 51% is systemic and ineluctable.
And again, the consensus is about [YES or NO] for any given new entry to the blockchain.
Again. The mathy thing is that the majority cannot, even in principle, be split, because it’s Y/N.
(I think the term ‘consensus’ is confusing you)
[Here’s a shout-out: https://en-academic.com/dic.nsf/enwiki/148691 ]
Johnny barges yet into another thread to hijack it and make it all about his #1 favorite subject, himself. Is this still Pharyngula or the John Morales Must Have All The Attention All The Time blog?
I am responding directly to other people, but it’s all about me in your estimation, AugustusVerger.
(Other people responding to me, ignored. Me responding to people responding to me, OOOOOOOO)
Basically, the issue is monopoly of five companies that hold over 80% of internet’s infrastructure. It allows for single points of failure. Doctorow wrote about it at length.
https://pluralistic.net/2025/05/13/ctrl-ctrl-ctrl/#free-dmitry
From your link, jo1storm:
“This week’s episode of “Who Broke the Internet?” focuses on those IP laws, specifically, the legislative history of the Digital Millennium Copyright Act, a 1998 law whose Section 1201 bans any kind of disenshittifying mods and hacks.”
What does that have to do with NFTs and blockchain?
(Also, from where I sit, the internet is not broken)
That IP law allowed the creation of monopolies by cutting all challengers at the knees and making it punishable by 5 year prison sentence if you make interoperable competing service by breaking any sort of “virtual lock”. In short, previously. if a company offered a bad product, a competitor could spring up with a better product. Since that venue is closed and big and crappy companies bought their own competitors, the end result is 5 companies controlling 80% of intranet infrastructure. Which is scary level of monopoly.
Maybe this article would be more understandable to you?
https://pluralistic.net/2022/02/20/we-should-not-endure-a-king/
Question was “What does that have to do with NFTs and blockchain?”
That IP law allowed the creation of monopolies by cutting all challengers at the knees and making it punishable by 5 year prison sentence if you make interoperable competing service by breaking any sort of “virtual lock”. does not answer it.
The topic is NFTs and blockchain, not the (allegedly) broken internet, which we are both using.
(It is irrelevant to the topic)
—
“Maybe this article would be more understandable to you?
https://pluralistic.net/2022/02/20/we-should-not-endure-a-king/”
What does that have to do with NFTs?
If the internet is under a scary level of monopoly, that seems to me that it’d make it easy to monopolize processing power and thus a higher proportion of the systems verifying the blockchain transactions.
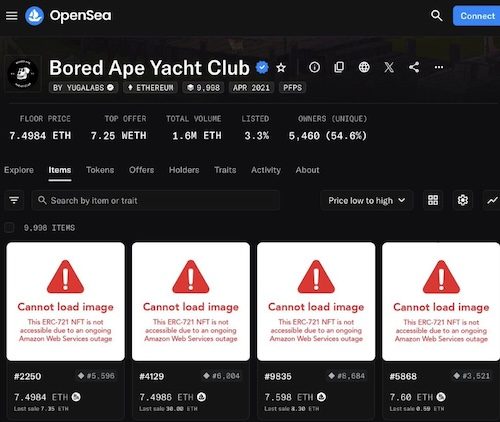
Not only monopolize processing power, but the actual storage. Specifically, NFTs don’t store the whole picture on the blockchain (on the decentralized distributed database) because its too large. Instead, the picture itself is stored on a storage like any other website which is most likely owned by one of the five. So one doesn’t need to attack blockchain at all, they only have to compromise THAT storage and mess with what the links point to or make them inaccessible.
For example, on the blockchain the link to the ape is http ama . ks/ape0129.jpg . An attacker could replace the actual file with something nasty so any “blockchain picture viewer” could either become a vector for viral infection. Or to do something easier but equally nasty, a vector for illegal pictures like CP. User wanted to see ape129 in their NFT collection? Well, that user just saw CP and it got cached in their browser too which means that user now has CP picture saved in a folder on their computer.
No.
“Not only monopolize processing power, but the actual storage. Specifically, NFTs don’t store the whole picture on the blockchain (on the decentralized distributed database) because its too large.”
Rubbish. A NFT is just one entry in the actual blockchain, not the blockchain itself!
All a NFT does is certify ownership and provenance for whatever digital asset.
For example, an Ethereum NFT token can be up to 8Kb — not exactly a lot of data.
As for processing power, that is a stupid thing to claim.
It would make some sense if participants did not have CPU cycles at hand, but they do.
They do not use cloud computing infrastructure for their verification!
(Also, I love you still think of NFTs as links to images. Could be any digirtal asset!)
[addendum… my own self-critique]
re: ‘All a NFT does’, I was too terse.
As per #3: “Yeah the block chain continues to fail to find a use outside of speculative “currency” or the NFTs. a lot of it comes down to the promises not living up to the realities of the problems they are claiming to solve (smart contracts seem dumber than just regular contracts, I am not storing medical information on the block chain, no company worth its salt is going to put its distribution network on a public resource they can’t control, and for what it is worth, using a block chain for any of that is more costly than the solutions that already exist and work exceedingly well…)”
Again, missing the substance. Those NFTs are programmable.
cf. https://iceteasoftware.com/nft-smart-contracts-and-nft-development/
(Using bored apes as an example for NFTs is like using cat videos (or, ahem, porn_ as an example of the internet)
“All a NFT does is certify ownership and provenance for whatever digital asset.
For example, an Ethereum NFT token can be up to 8Kb — not exactly a lot of data.”
And that digital asset is usually not on the blockchain itself. Which is where the monopolies come into play.
“(Using bored apes as an example for NFTs is like using cat videos (or, ahem, porn_ as an example of the internet)”
Sure. Let’s talk about “rugpulls” instead.
What? No.
The digital assets may reside on any retrievable location, on-chain (if small enough), or off-chain, where they would be typically referenced by resolvable URLs.
Also, they can be programmable — thus ‘smart contracts’.
Any asset you can point to digitally can be assigned provenance and ownership.
That’s the point of NFTs.
(Your quip does not address that; you still think they are ape images, no?)
[I mean, anyone can con anyone else out of their assets. Blaming the ledger for that is, well, kinda unfair]
“off-chain, where they would be typically referenced by resolvable URLs.”
99.9999% of NFT digital assets reside off-chain though, so let’s talk about those.
“Any asset you can point to digitally can be assigned provenance and ownership.
That’s the point of NFTs.”
I don’t understand your point here. If 99.9999% of NFT assets reside off-chain (and they do) then the security of the chain itself is less relevant than the security of the place where they reside at and that is my point. Correct?
“[I mean, anyone can con anyone else out of their assets. Blaming the ledger for that is, well, kinda unfair]”
Technically correct, the best kind of correct. You can con people of their assets irl too. The thing is, when the cons are so endemic to the space that they get their own nickname of “rugpull” , I think there is the issue with the space itself. One issue is the nature of smart contracts. They are not smart enough to detect cons. You need people for that.
“I don’t understand your point here. If 99.9999% of NFT assets reside off-chain (and they do) then the security of the chain itself is less relevant than the security of the place where they reside at and that is my point. Correct?”
No. As you note, the NFT is not the asset.
Both are relevant, and more to the point, even if the asset is copied by someone or disappears, the NFT still shows its provenance and ownership.
Anyway, yes. NFTs are still a thing, because it’s a niche technology that can have use cases.
Just because it’s been used frivolously doesn’t mean it’s frivolous in itself.