Strava (a fitbit competitor health bracelet tracking device) released “heat maps” of their data-sets. I suspect that is going to change fairly quickly, but the information security world has been having a ton of fun with it.
Information security practitioners are, among other things, supposed to think about what can happen if you combine data to produce side-effects (sometimes called “side-channels”) – the recent Meltdown [wik] and Spectre bugs are another example of side-effects revealing more information than they should. Strava’s data-set is keyed to GPS coordinates, which means you can do things like: (Nathan Ruser is an analyst who tracks conflict zones using 3rd party intelligence [ruser])

Turkish patrols near Manbij in Syria
From a military standpoint, it’s particularly useful because not only does it show your target’s track, it shows the frequency. If you were going to plant an IED to reap some Turkish troops, where would you plant it? Where the heat-map is yellow, of course. [stderr]
We should probably expect a great deal of new activity in terms of de-activating google map-zones and Strava will probably pull down their service for other map regions. Ultimately, though, this is a fruitless effort because every cell phone, iPhone, and toy drone has got GPS in it, and reports coordinates back (constantly) to some server somewhere. Next up, we’ll probably have a big scare in which the Russian intelligence services embed GPS tracking into a fun smart-phone app, so they can get their own GPS tracking stack without having to worry about Strava providing it.
Waze and Apple already do this in their mapping apps: if they see large numbers of iPhones on a particular stretch of road that normally flows at 50-70mph, and the phones are not moving minute over minute, it infers that there is a traffic slow-down and starts re-routing people. Thus, “big data” giveth and “big data” taketh away.
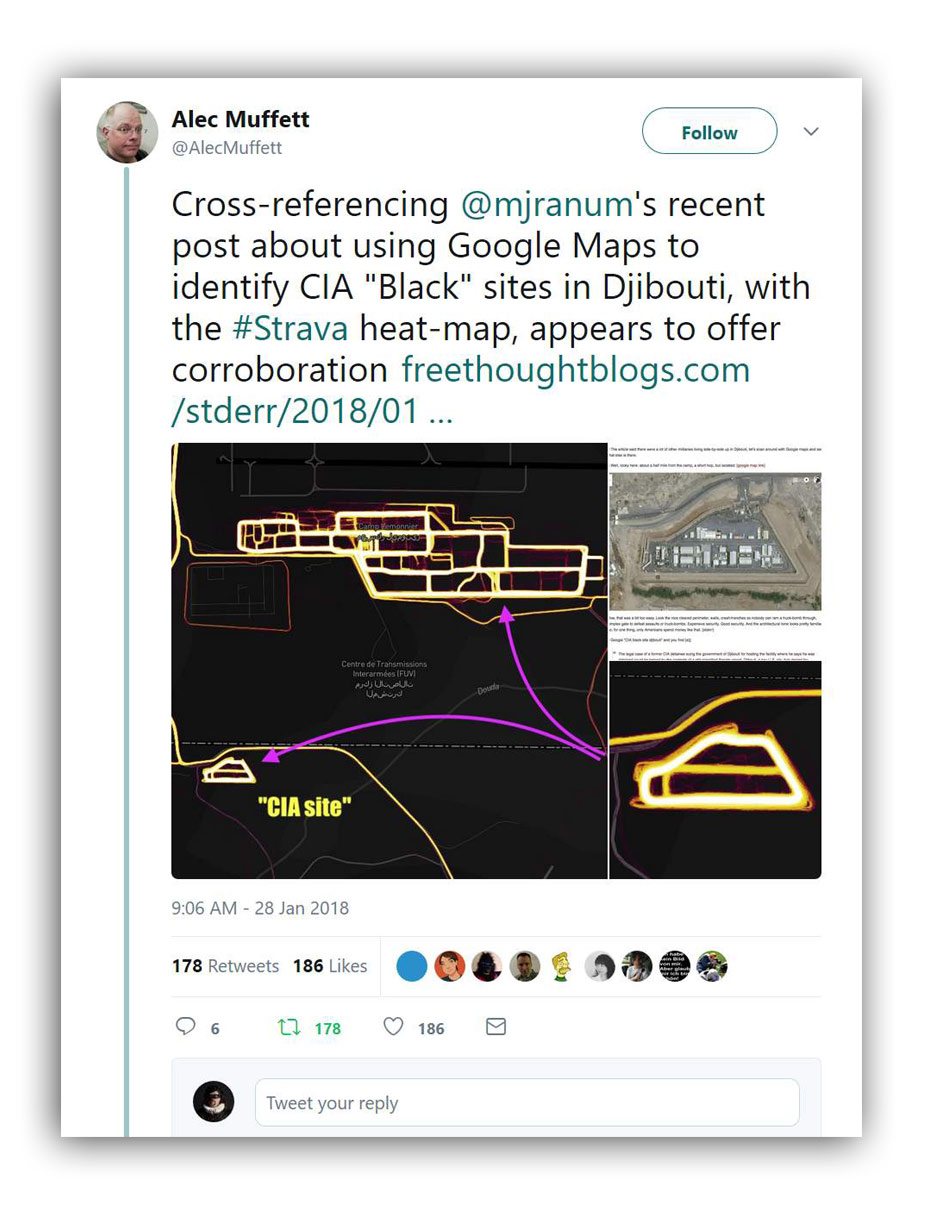
My old buddy Alec Muffett apparently reads this blog, because he took the map coordinates I posted for the CIA black sites in Djibouti and checked them in the Strava database. [stderr]
Dino Brugioni is a name most of you will not have heard. For me, he kept cropping up in very unusual places: in books about the CORONA program, doing analysis of grain-structure in the print of Lee Harvey Oswald holding the newspaper and the rifle, during the Cuba Missile Crisis, etc. [wikipedia]

It turned out that Brugioni was one of the founders of a very secretive agency known as NPIC (National Photo Interpretation Center) – NPIC was created, like NRO, to handle the increased amount of technical intelligence (NSA still owns comms intelligence) when the U2 and CORONA program began to generate huge amounts of data. There was a certain understandable fear that if CIA was allowed to be the primary collector of all the data, nobody else would ever get to look at it and CIA would become like a camera-driven version of the NSA, only with a license to kill.
Anyhow, Brugioni writes in his excellent book Photo Fakery [amzn] about how they were able to determine which Soviet missile platforms in Siberia had working missiles: they were the guarded ones, and guards make tracks in the snow. He used a similar technique to analyze Soviet missile batteries in Cuba during the missile crisis – you can see who is going where and how often by the tracks in the dirt.
As David Byrne would say: “same as it ever was.”

In 1979 Dino Brugioni attempted to answer the question of whether allied photoreconnaissance was able to determine the purpose of the nazi death-camps. If you recall, one of the fig-leaves the allies hid behind was “nobody knew” so “nobody did anything.” Elie Wiesel used to ask what would have happened if there had been some attempt to parachute soldiers in to stabilize the camps, or to disrupt the trans-shipping of jews. Well, Brugioni’s analysis is pretty chilling, but interesting, if you want to get an idea of how this sort of thing is done. [brug]
Spook-hunters all over the internets are having a field day with this data-set. Good! Secrecy is usually used to defeat oversight.
Update: What I named as a CIA black site in Djibouti is apparently an Italian base. It’s fascinating to see the kind of ground-based identification you can do: [twit]


I hardly think the Allies cared much for what happened in the camps. Neither the British nor the Americans have balked at the slaughter of civilians at any other time.
One would have imagined the military to be aware of this issue already, and they sort of were.
https://www.theguardian.com/technology/2018/jan/29/strava-secret-army-base-locations-heatmap-public-users-military-ban
John Morales@#2:
One would have imagined the military to be aware of this issue already, and they sort of were.
Sort of, yes.
There is still huge amounts of data, it’s just being collected by “trusted” collectors – like Apple, Google, etc. The stuff you could get from iPhones is way more interesting than the Strava; they just don’t publish it. But I’m sure the FBI can get it, and the NSA already does (what do you think all those drone strikes are based on?) Cell phones appear to not just track, they are full of apps that report back to – somewhere in the cloud.
I remember one meeting I had at NSA HQ (OPS2) back in 1992 – the security at the gate went through briefcases and pulled out anything electronic. I wonder if they still do that. According to some Strava maps I’ve seen, the answer is: no.
So, if you have a certain user handle, you can watch them in Strava, if I understand correctly. It would seem that all you’d have to do is observe individuals going in and out of an FBI field office and correlating the user handles, and you’ve got a cop heat-map tracker. I’m not sure how real-time the data is, but it’d be pretty useful to be able to see where all the cops are grouping up before a raid. One could track ICE, for example.