…. that would come from Washington, if the North Koreans were launching cyberattacks against US nuclear assets, and strategic missile development programs.
Some of this is old information; I didn’t post about it last year because I considered it speculative and was hoping for better attribution (or a confession a la Stuxnet): apparently the US has been carrying on a “cyberwar” against North Korea’s nuclear program and missile development program for some time.
The New York Times, a US propaganda outlet that trades crunchy nuggets and access for its journalistic virtue, carries a story about how the Obama administration began efforts to waylay the North Korean technical program. The Times agreed not to print anything, because when the National Security advisor gives you a Snowden-like dump of secrets, you don’t print them until he says “roll over” and pats your belly. [New York Times]
There were many options, some drawn from General Dempsey’s list. Mr. Obama ultimately pressed the Pentagon and intelligence agencies to pull out all the stops, which officials took as encouragement to reach for untested technologies.
The North’s missiles soon began to fail at a remarkable pace. Some were destroyed, no doubt, by accident as well as by design. The technology the North was pursuing, using new designs and new engines, involved multistage rockets, introducing all kinds of possibilities for catastrophic mistakes. But by most accounts, the United States program accentuated the failures.[nyt]
Allegedly this song is about how amazing North Korea’s CNC Machines are. I am waiting for a track by Kanye West about how awesome braiding machines can be. [source]
It’s hard to know if this is real; it’s possible that the US is simply goosing the North Koreans into shooting a few of their researchers, and spending a huge amount of time going over their computer systems. When you think about some of the systems bugs that the NSA ‘Equation Group’ has developed – bugs that lie dormant in the firmware of hard drives and motherboard BIOS – it would be difficult indeed to build a system you could trust if it had any components from Intel, Microsoft, Samsung, Seagate, Western Digital, or Nvidia. There are a huge number of attack-points: what if some CAD controller or modelling software detected a certain network locale and caused parts to be slightly off balance? What if a closely secured computer facility that was proof against network attack (like the Iranian centrifuge systems at Natanz) was corrupted by an agent-in-place higher up the supply-chain, who provided a specially configured system? If you look at the way the advanced malware like Stuxnet works, it can be tailored to be extremely specific: if you are on this particular IP address subnet and you are talking to that model of a particular programmable logic controller (PLC) then give it data that’s slightly off.
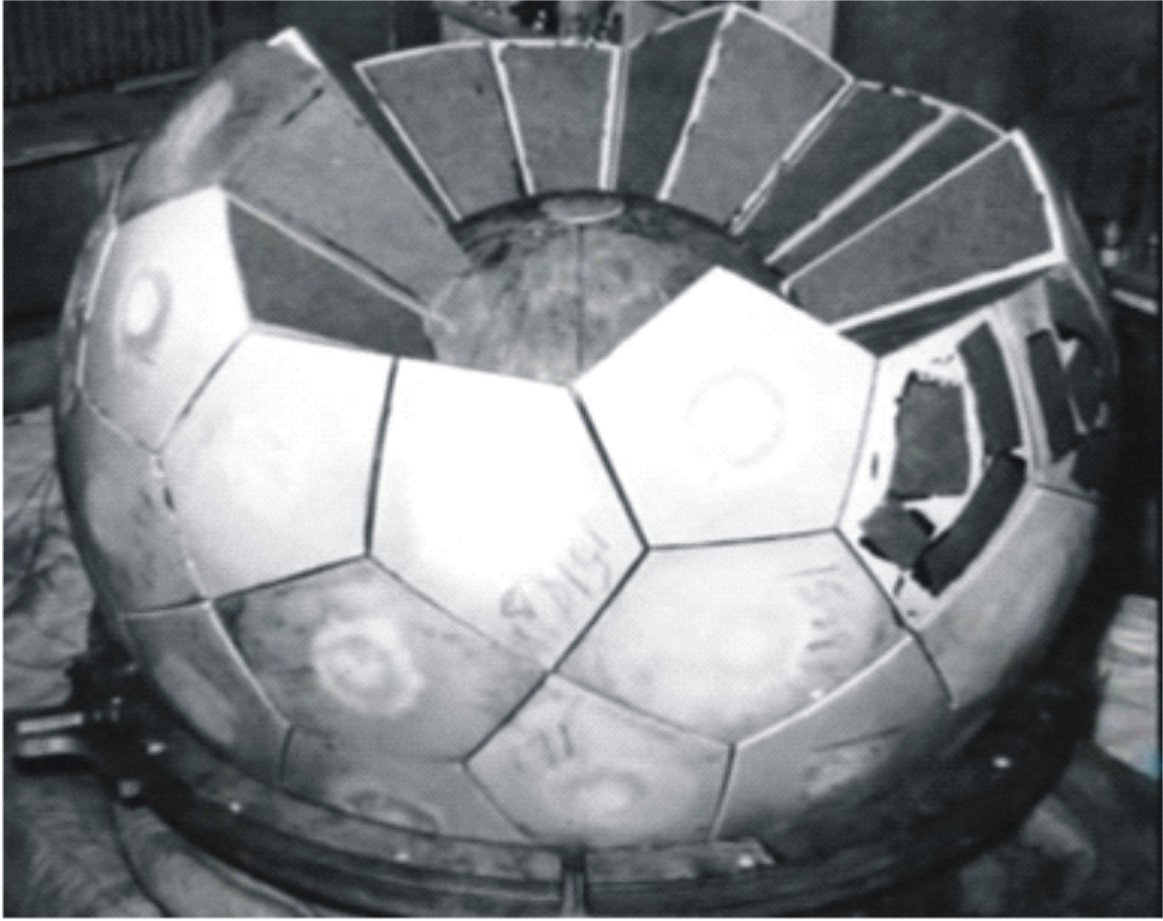
high explosive lenses being assembled in the Trinity “gadget”
Nuclear weapons primaries (the A-bomb that ignites the H-bomb using radiation pressure to trigger fusion) require extremely accurately machined high explosive lenses. Most countries currently making nuclear weapons are using various compositions of very hard, fairly inert, plastic high explosives that can be machined to a close tolerance. If the North Koreans were using a CNC machine that was slightly corked (or a corked version of the software used to design the lenses) you’d wind up with a fizzled explosion – just like the North Koreans repeatedly experienced. As I described [stderr] the whole process of “weaponizing” a nuclear weapon involves making the components to tighter and tighter tolerances; that’s the same problem a ballistic missile designer has to deal with – and a few errors compounding here and there can cause maddening failures, especially when the system that’s supposed to measure the tolerance is also corked. Imagine if your CNC machine was off, and your means of measuring your output were also off: everything would look fine until it failed catastrophically.
The evidence was in the numbers. Most flight tests of an intermediate-range missile called the Musudan, the weapon that the North Koreans showed off in public just after Mrs. Clinton’s warning, ended in flames: Its overall failure rate is 88 percent.
Nonetheless Kim Jong-un has pressed ahead on his main goal: an intercontinental ballistic missile. Last April, he was photographed standing next to a giant test-stand, celebrating after engineers successfully fired off a matched pair of the potent Russian-designed R-27 engines. The implication was clear: Strapping two of the engines together at the base of a missile was the secret to building an ICBM that could ultimately hurl warheads at the United States.

What kind of computers are in that machine? Probably not a great idea to publish what you’re using, Kim, OK?
I have to say it is thought-provoking when Russian components work and North Korean components don’t. Wait, did someone just say that the Russian R-27 design found its way somehow into the hands of the North Koreans? Presumably the Russians aren’t selling R-27s on Etsy.[armscontrolwonk] This exposes a point that often remains hidden: a lot of countries are making a lot of money selling the North Koreans stuff. CNC machines, PLCs, flow-forming machines [armscontrolwonk] and so on. The point is: there is a long and complicated history of selling other nations weapons-making gear that doesn’t quite work right, and then being horribly surprised when they eventually figure out how to make it work.
Bizzarely, the Times shifts to “on the other hand” after following the establishment’s party line through most of the article:
Once the United States uses cyberweapons against nuclear launch systems — even in a threatening state like North Korea — Russia and China may feel free to do the same, targeting fields of American missiles. Some strategists argue that all nuclear systems should be off limits for cyberattack.
No, really? Remember: the US is the country that is constantly worrying out loud about how some nation state could attack its power “smart grid” systems, data networks, or spy on its defense secrets. I often wonder how much of that deep concern is motivated by a crawling certainty that the US has invited that sort of retaliation. For one thing, attacks on nuclear systems (as well as power systems and hydroelectric systems) are war crimes under the Geneva Conventions, protocol II (Rule 42) but the US has already openly blown past that with the Stuxnet attacks on the centrifuges at Natanz and the nuclear reactor at Bushehr. Ultimately, I think the reason the US hasn’t come under such attacks is because the US has adopted the position that cyberwar is a weapon of privilege: we can use it on you but, as Mr White says in Reservoir Dogs:

Globalsecurity.org – report on Nodong missile failures. [link] Before we accept that these failures are a result of cyberwar, we should remember that the US’ early missile development wasn’t exactly a cakewalk, either. On the other hand, missile development was a new science at the time, and the North Koreans have advantages that the US didn’t have in the 1960s: CNC machines (assuming they are not corked) and availability of pre-tested designs, such as rocket motors and guidance systems.
A lot of countries made a lot of money (most specifically Siemens AG) selling off-the-shelf Uranium low-level enrichment gear, which is where A.Q. Khan learned to make centrifuges. “Civilian” nuclear reactors (like the Iranian one at Bushehr) [wikipedia] used to be for sale: the initial construction was done by German companies. (When Israel bombed the Iraqi nuclear facility at Osirak, they killed some French engineers) The art of selling stuff to colonials has not gone out of style; it’s still an important part of The Great Game.
This is some interesting stuff on North Korean rocket motors.[38north] Where are they getting this tech?

Do not put pictures of your cascade’s PLC configuration on television, OK?
If you’re interested in the level of detail to which Stuxnet can be analyzed from open source data, see [Langner] Ralph Langner has pretty much devoted his career to figuring out what Stuxnet did. Very worth a read!

This made me wonder if nuclear powers hacking the living hell out of each other is the only viable path to actual disarmament. By the end of it the weapons simply wouldn’t work when launched but nobody would know until the button was pressed. The ICBMs would just go ‘fssst’ and stay in their silos. The warheads, meanwhile, might actually be sitting in some out-of-the-way bunkers in Alaska / Siberia / … because the inventories were hacked, too.*
Well, if Anonymous or some other bored group of hackers need a hobby project, here you are. Just make sure you hit every nation before one of them tries to end everything. Might be a tight deadline.
*World peace will arrive when all heads of state are brougth together by that great unifier, the shared technical glitch: “Hey, Vladimir, Donald here. Listen, we just tried to nuke you but the things… missiles aren’t working. Yes, our nukes aren’t working. Are yours? Oh, you’re testing them now, are you? Great, should I wait or do you want to call back?”
komarov@#1:
There would probably be some wonk at RAND corp who’d come up with a statistical model for how to preserve a balance of terror in an uncertain reliability environment.
Unfortunately, the US appears to have been far enough ahead to have thought of some of the stuff that the rest of the world didn’t. I remember back in the 1980s the NSA and CIA were building operating system releases from scratch and reviewing patches for backdoors.* I’d be fairly certain that process has stopped, because it never was practical, but it points to a general concern (and a good one!) with trusted software distribution and supply chain tainting. US sources first started voicing concerns about hardware from China back in the late 90s — probably around the time that the US was compromising export devices — but that’s probably coincidence.
If nukes became unreliable, it would just usher in an era of testing and torture, I’m afraid.
(* I know this because one of the things I did when I worked at Digital was check the build process and cut the source tape for the ULTRIX release that went to those guys.)
Yes, clearly I wasn’t cynical enough. One of the first ‘worst case scenarios’ identified at the start of the Cold War probably covered that eventuality and spared no expense mitigating the risk. Risk management may be something of a double-edged sword when it is applied to nuclear reta… beg pardon, deterrence. No doubt everybody on the planet would be very disappointed if one side failed to nuke the other during an exchange. If that were to happen noone would ever take the smouldering, radioactive ashes of [Nation] seriously again.