
The lulzsec logo
I haven’t hidden how unimpressed I am with the FBI/CIA/NSA’s joint report that alleges Russian hackers interfered with the 2016 elections. In my opinion, the ‘evidence’ they present is painfully thin, and mostly bad or inaccurate.
Let’s have a look at some of the quality of evidence that the FBI has been able to present in other hacking cases.
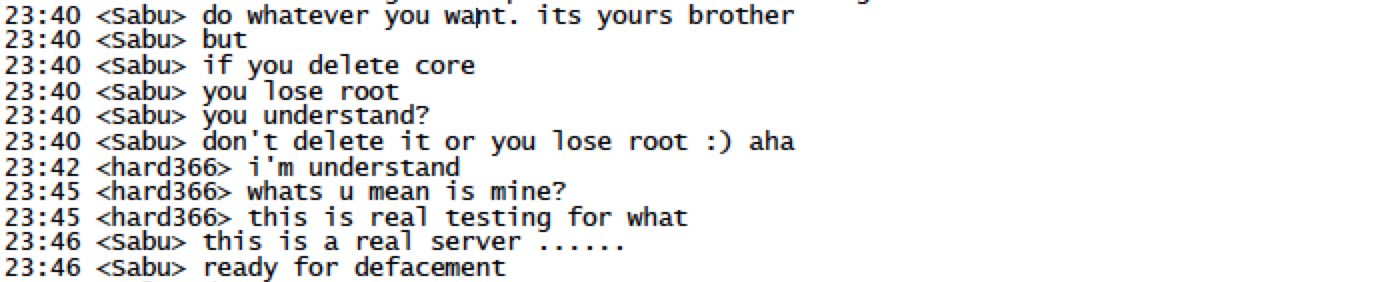
‘Sabu’ (Hector Monsegur) coaching someone how to hack a police website in Brazil[1]
The chat above was allegedly recorded January 23, 2012. The Brazilians haven’t said anything (their systems logging is probably as bad as the US’ government agencies are) but there have been plenty of published incidents of various hacker groups successfully hacking Brazilian police:

Hacked Website of Brazilian National Police[2]
03:45 <&Sabu> they doing another 4 gov.br defacements
03:45 <&Sabu> that we at #antisec gave them
03:45 <&Sabu> so wait for those
03:45 <&Sabu> and
03:45 <&Sabu> we gave them root on brazils biggest media site globo
03:45 <&Sabu> so lets see how they handle it
03:45 <redacted> no
03:45 <redacted> no way
03:45 <&Sabu> yup
03:45 <redacted> root on globo???
03:45 <redacted> hahahahahahahahhahahahaha
03:45 <&Sabu> ;P
03:45 <redacted> HAHAHAHHAHAHAHA
03:45 <redacted> epic win
03:46 <&Sabu> they might not deface it but study it, get passes etc
03:46 <redacted> but epic
03:46 <redacted> u need to follow that sabu
03:46 <redacted> that will be the biggest event in brasil ever
03:46 <redacted> ask to mention us
03:46 <&Sabu> yup
03:46 <redacted> epic lulz
03:47 <&Sabu> they will throw #antisec in it
03:47 <redacted> brazilians will go crazy
So here we see an FBI confidential informant giving some other hacker administrative access to “Brazil’s biggest media site” Globo. By now you should know what I’m going to post next, right?
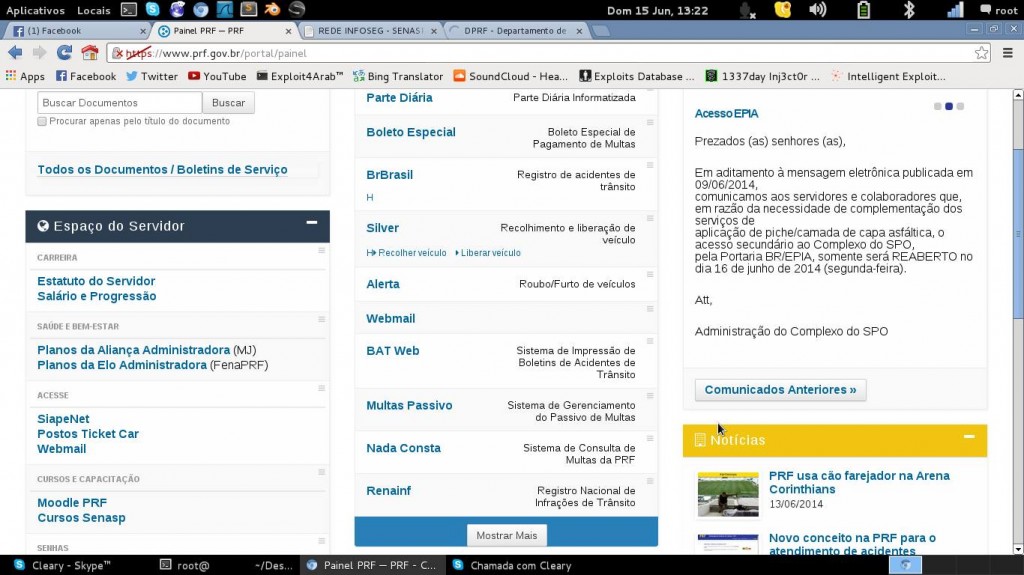
Control panel for Globo server[3]
The FBI would have been in prime position to notify the Brazilian targets so they could respond more effectively.

Sabu
… But that’s not how it’s done. Remember, this is the FBI that produced an utter garbage report about alleged Russian hacking, but keeps and eventually leaks this kind of evidence about its own activities regarding attacks it inspired on other nations.
This is why some of the more experienced computer security analysts on the internet raised their eyebrows at the flimsiness of the FBI’s attribution to North Korea and later to Russia. We know they’ve got better data. We know the hackers do. One of the reasons I sometimes suspect that the FBI doesn’t present real evidence is because a) they haven’t got any and b) they know that if they try some hacker from New Jersey is going to post their screenshot of the DNC email server, that they took and timestamped while they were doing the hack. It would be entirely in keeping with the sociopathic hacker mind-set to post something like that just to show the FBI was wrong, if someone else was trying to take “credit” for their kill.
Let’s also talk about how the “FBI Informant” story evolved. If you read the New York Times story about Sabu, it reads:
WASHINGTON — An informant working for the F.B.I. coordinated a 2012 campaign of hundreds of cyberattacks on foreign websites, including some operated by the governments of Iran, Syria, Brazil and Pakistan, according to documents and interviews with people involved in the attacks.
Exploiting a vulnerability in a popular web hosting software, the informant directed at least one hacker to extract vast amounts of data — from bank records to login information — from the government servers of a number of countries and upload it to a server monitored by the F.B.I., according to court statements.
Notice the nice way the Times gives the FBI the benefit of a massive doubt? They just say “an informant”.
Let me explain to you how that went down:
- The FBI watched and monitored Sabu for a week or more (during which time Sabu was committing crimes)
- The FBI showed up on his doorstep and arrested him
- The FBI then “turned” him and allowed him to continue committing crimes, by threatening to take Sabu’s kids away
The New York Times is again showing its desperate desire to please its masters, by referring to Sabu as “informant” because “agent” has legal meaning. An “agent” is someone who is doing things on your behalf. An “informant” is someone who is telling you things. The New York Times deliberately used the FBI’s preferred term, which down-plays their role in events.
The FBI had many chances to stop Sabu’s actions but decided – instead of acting like a law-enforcement agency – to act like a counter-intelligence agency and run an “agent in place” within a hacking group. They also felt it was more important to keep Sabu’s kids in a dangerous criminal environment, than to try to do anything to help them.
Here’s one crazy possibility that bothers me a lot when I think about it: what if the CIA/FBI/etc actually have pretty good evidence of the Russians hacking the DNC, they’re just not presenting any of it because it will show that they stood by, with their arms crossed, and watched the whole thing and said nothing. What if there is evidence, but it’s evidence that the FBI failed to do its job?
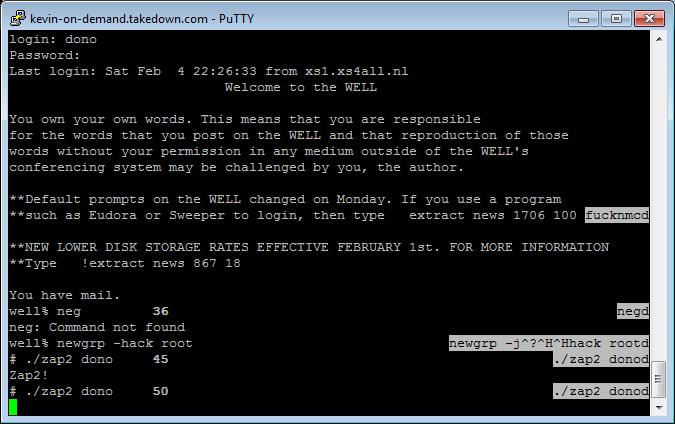
(from kevin on demand, by Tsutomu Shimomura)
The FBI does this a lot. In my article about Wikileaks, Lamo, and Mitnick, it is clear that the FBI had substantial intelligence about who was saying what to whom and when. The chat-logs from Lamo (who was probably on probation at the time) were used as attribution against Chelsea Manning. See? The FBI does know how to do attribution right.
When you’re breaking apart a big hacking operation, there are tons of artifacts left behind. Think back to other hacking cases you’ve read about: there are artifacts. I’ve generated my share[5] and there are many many examples of people collecting solid attributable evidence for attacks. Tsutomu Shimomura famously recorded and animated Kevin Mitnick’s attacks for a while, it was compelling evidence.* When Kevin Mitnick got his copy of the TCP sequence-guessing attack from his hacker friend in Israel (jsz) they communicated by email using a shared server (which I happened to be the administrator of, so I turned all the emails over to the Secret Service) – and that’s the point: unless there’s utter incompetence of the highest degree going on, all around, there will be artifacts relating to any incident. In fact, there will be artifacts that the FBI would present as evidence if the case ever went to trial – which is why I am extremely skeptical of claims regarding Russian hacking of the 2016 election: I want to see the evidence. At the very least, convince me the hacking wasn’t an FBI operation.**
I’ll let Sabu have the last word:
“These niggas don’t care if they stop Anonymous at the end of the day,” Monsegur told Sanguinarious. “Their priority is to make the FBI look good at the end of the day.”
 I remain on record as being skeptical that the North Koreans had anything to do with Sony breaches. Sony had been coming under years of dedicated attacks and had been repeatedly breached prior to the “North Korea” incident. I have observed repeatedly that hackers will penetrate a target, play around inside it for years, and then finally get tired enough that they smash a few windows when they leave. If you think about it for a second, that’s the strategy that makes sense: you don’t want to tip anyone to your presence while you’re still working the target, and once you have tipped your hand then you should assume that there are packet vaccums and logs being collected to try to figure out what’s happening now that it’s too late. The sensible strategy is you leave, and never come back, and the next hacker that walks in there is more likely to have a hard time or be detected.
I remain on record as being skeptical that the North Koreans had anything to do with Sony breaches. Sony had been coming under years of dedicated attacks and had been repeatedly breached prior to the “North Korea” incident. I have observed repeatedly that hackers will penetrate a target, play around inside it for years, and then finally get tired enough that they smash a few windows when they leave. If you think about it for a second, that’s the strategy that makes sense: you don’t want to tip anyone to your presence while you’re still working the target, and once you have tipped your hand then you should assume that there are packet vaccums and logs being collected to try to figure out what’s happening now that it’s too late. The sensible strategy is you leave, and never come back, and the next hacker that walks in there is more likely to have a hard time or be detected.
Take for example Nortel, which was hacked in an ongoing breach for nearly 10 years. Of course it was the Chinese. Yeah.

The top chat script shows Sabu telling his interlocutor how to use some kind of backdoor.
When he says “if you delete core you lose root” what he means is: “if you delete the file named ‘core’ you lose the ability to get privileges on the system.” i.e.: “root”. “core” is a file created when a program generates a certain type of error, memory alignment, attempt to access out of memory (a wild pointer) or is sent a signal SIGCORE, which tells it to produce a debugging output file. Sabu has, presumably, created some kind of shell with ‘setuid’ owned by user zero “root” someplace on the system. That way, to get privileges, you just run ./core and your backdoor is hiding as a debugging output file.
This is really amateurish! Kevin Mitnick, back in the 1990s, was naming his backdoor ‘zap2’ (see above) but, so what. A competent system administrator audits for the appearance of setuid root files. I first did that back around 1986 or so, using a shell command like:
find / -type f -perm -4000 | sort > setuid.new diff setuid.old setuid.new > new_setuid mv setuid.new setuid.old if [ -s new_setuid ]; then mail -s "new setuid files" mjr@drongo < new_setuid mv new_setuid archives/`date +%m.%d.%y` fi
Some system admins automatically clean up ‘core’ files (find / -name core -exec rm -f ‘{}’) which would have deleted Sabu’s backdoor without detecting it.
I guess they don’t make system administrators like they used to. They do make hackers like they used to; they’re still using entry level tricks from the 80s. I actually saw more sophisticated stuff than that in the 80s…

(* For someone who spends as much time in front of a keyboard, he’s a lousy typist!)
(** Remember, “Deep Throat” was deputy director of the FBI at the time when he disclosed secret information to Time Magazine and The Washington Post, directly resulting in the toppling of the Nixon regime. The FBI has been known to play politics before, and since.)
[1] Motherboard: Exclusive: How an FBI Informant Helped Anonymous Hack Brazil
[2] Techworm: Website of Brazilian Federal Police Hacked and Defaced
[3] Hackread: Anonymous Hacks Brazilian Government, Police, Court, Globo TV, and Cemig Telecom
C|Net: Nortel Hacked for Years but Failed to Protect Itself, Report Says
New York Times: FBI Informant is Tied to Cyberattacks Abroad
[4] WIRED: Manning-Lamo Chats Revealed (DO NOT read the transcripts. You will see what a painful naif Manning was, and it’s heart-rending to read how she expected to be able to get out of the situation she was going into, and get a job … Instead, solitary confinement and torture.)
[5] Marcus Ranum (Tenable Blog): Attribution is Hard, Part 1

Re footnote [4] – problematic pronouns persist.
Pierce R. Butler@#1:
Thanks! Fixed.
I hope that my screwing that up isn’t an indication of some mental block on my part. I think it’s a side-effect of my being focused on my topic, but, ugh. I will be more careful.
Marcus Ranum @ # 2: I think it’s a side-effect of my being focused on my topic…
Just as we tend to notice gender first, we hang on to it hardest. [NB, folks, I said tend!]
When a friend changes a name, address, appearance, or preference, I hardly ever mis-state that later – but when someone changes [presentation of] gender, I have to fight the previous description for months or more.
As for the Topic … I hope we get to hear Christopher Steele’s view on the Kremlin’s ace hackers before the current 00_ catches up with him.
Pierce R. Butler@#3:
I hope we get to hear Christopher Steele’s view on the Kremlin’s ace hackers before the current 00_ catches up with him.
I don’t see any reason to believe that Steele would know anything about hackers. He was an SIS officer and it sounds like he was well-connected with a network of people willing to tell him things, but that doesn’t mean that he’d have any way of knowing about hacking, or entrapment operations. It sounds to me like he was collecting speculation. There’s nothing wrong with that but – as usual – intelligence needs to be graded based on its reliability (sources, methods, timing) and from the sound of it, we’re looking at a waffle cone full of waffle-flavored ice cream with waffle chunks and waffle sauce topping.
A bit of research indicates that some people believe the UK press was given a D Notice (which is, basically, a legal way the UK intelligence apparatus can tell journalists “STFU” and have them obey) regarding Steele. They’re probably trying to wind things back and find out if Steele is still pumping his old network, now that he’s gone private. That would be a huge no-no, of the type which the KGB had specific ways of showing their “disapproval” but in the UK might result in a Strongly Worded Memo.
The people who should be giving their views about the alleged russian hackers are, of course, the FBI, CIA, and NSA. They remain strangely empty of information. The more I think about this, the more I like my theory that they are being quiet because they had information about the hacking for some time, and didn’t tell anyone, which makes them look just as bad or possibly worse. That’s unfounded on my part, it’s just a guess, etc. Of course, it would be easy for the various players involved to resolve these questions, yet they continue to choose not to. Trump, when inaugurated, could do something delicious and order the FBI/CIA/NSA to publish their evidence. That would be LOLriffic.
Marcus Ranum @ # 4: I don’t see any reason to believe that Steele would know anything about hackers.
He would know a fair amount, I think, about how the Russians kollect their kompromat.
… some people believe the UK press was given a D Notice (which is, basically, a legal way the UK intelligence apparatus can tell journalists “STFU” and have them obey) regarding Steele.
I couldn’t find anything about it on the Guardian’s front page, nor that of Theh Times; saw a good backgrounder and Head of MI6 used information from Trump dossier in first public speech at the Independent. Am too sleepy-lazy to search further; others can do it better.
Would Steele really go into hiding from a Strongly Worded Memo? (Yes, his face is already out there.)
… I like my theory that they are being quiet because they had information about the hacking for some time, and didn’t tell anyone, which makes them look just as bad or possibly worse.
As we’ve seen since 9/11, that sort of ass-covering produces lots of informational (& other) collateral damage.
Pierce R. Butler@#5:
He would know a fair amount, I think, about how the Russians kollect their kompromat.
My knowledge of tradecraft is minimal, but my impression was always that those type of operations involved placing the target in a hotel room or other location was was professionally wired for sound and video. Hacking would only make sense if you were dealing with someone like Anthony Weiner who carried around a bunch of evidence on his laptop (though in Weiner’s case I gather it was pretty easy to get that evidence, all you had to do was pretend to be female and act interested)
Would Steele really go into hiding from a Strongly Worded Memo?
No, but the UK press would STFU and stop digging into Steele’s career and network. Him going into hiding might be because he wanted to avoid the press attention, and it might be because he was concerned that the Russians would, you know, send him a “cease and desist” KGB-style. But they probably don’t care, really. If someone tops off his salt shaker with polonium-210, then we’ll know the Russians actually were pissed off at him. My guess is that they are laughing their asses sore over the whole incident. It reveals everyone involved to be a bunch of yutzes.
As we’ve seen since 9/11, that sort of ass-covering produces lots of informational (& other) collateral damage
Yup. I don’t know who said it, but – never attribute to conspiracy what you can attribute to bureaucratic incompetence and infighting. Hm, it’s maybe Ranum’s Variant of Hanlon’s Razor.
The Register: Steele D-Notice
I’m not sure how they work, but I assume they’re sort of like a US National Security Letter: the first rule of NSL is you do not talk about NSL. The second rule of NSL is you do not talk about prior restraint. The third…
Apparently Steele may have worked with Litvinenko. So, while I wasn’t trying to be funny, I wound up actually being tasteless.
By the way, you’ve got to love the press; what a bunch of douchebags. At the same time that they are talking about how Steele may be in danger, they add:
Christopher Steele fled his home in Surrey
and elsewhere that he fled:
his £1.4million Surrey mansion
If any of you haven’t seen “The tall blond man with one black shoe” (Pierre Richard) it’s a pretty charming lighthearted movie about spies. It has some of my favorite silly spy tropes, ever and I suspect that the street outside of Steele’s house is much like the airport scene in the movie: spies watching spies watching spies watching the neighbor watch the cat.
Well, they still work…
Marcus Ranum @ # 6: … those type of operations involved placing the target in a hotel room or …
Classic technique going back way before Felix Dzerzhinsky, as documented in Fleming’s well-known history From Russia with Love. But, surely, hardly the only arrow in FSB’s quiver.
… in Weiner’s case I gather it was pretty easy to get that evidence, all you had to do was pretend to be female …
Certain Moscow operatives would not even have to pretend.
Him going into hiding might be because … he was concerned that the Russians would, you know, send him a “cease and desist” KGB-style. But they probably don’t care, really.
A source close to Mr Steele said he was “horrified” when his nationality was published and is now “terrified for his and his family’s safety”. So sayeth the Torygraph, so a good helping of salt is advised – but I suspect everybody who knew Steele back in Putinstan knows what that “source” is talking about.
… Ranum’s Variant of Hanlon’s Razor.
What the hell kind of Razor leaves its area of application more bushy and tangled than it was before?